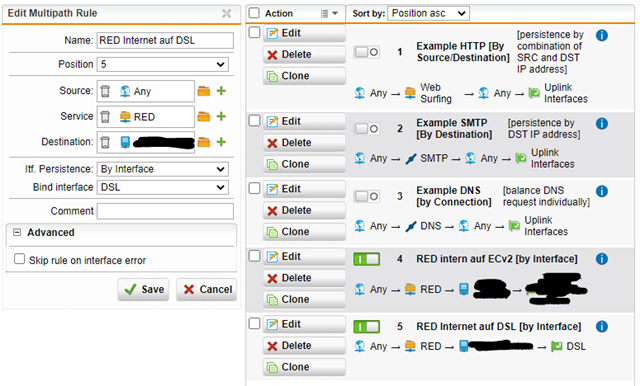
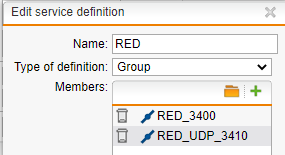
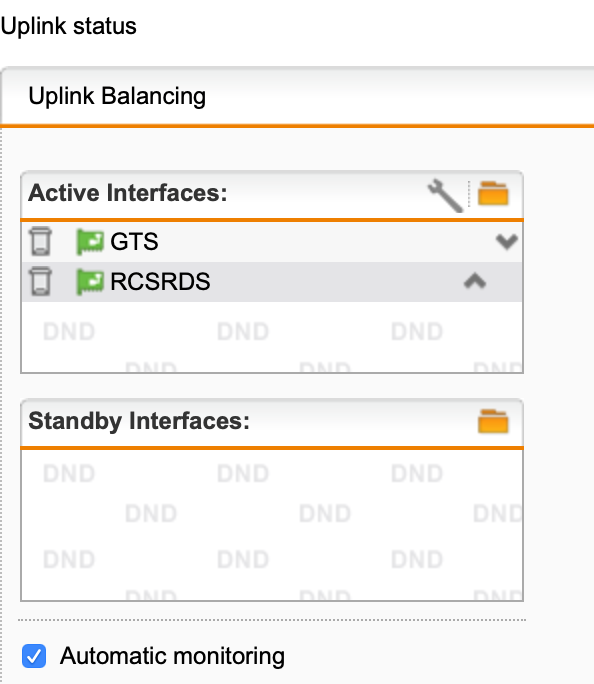
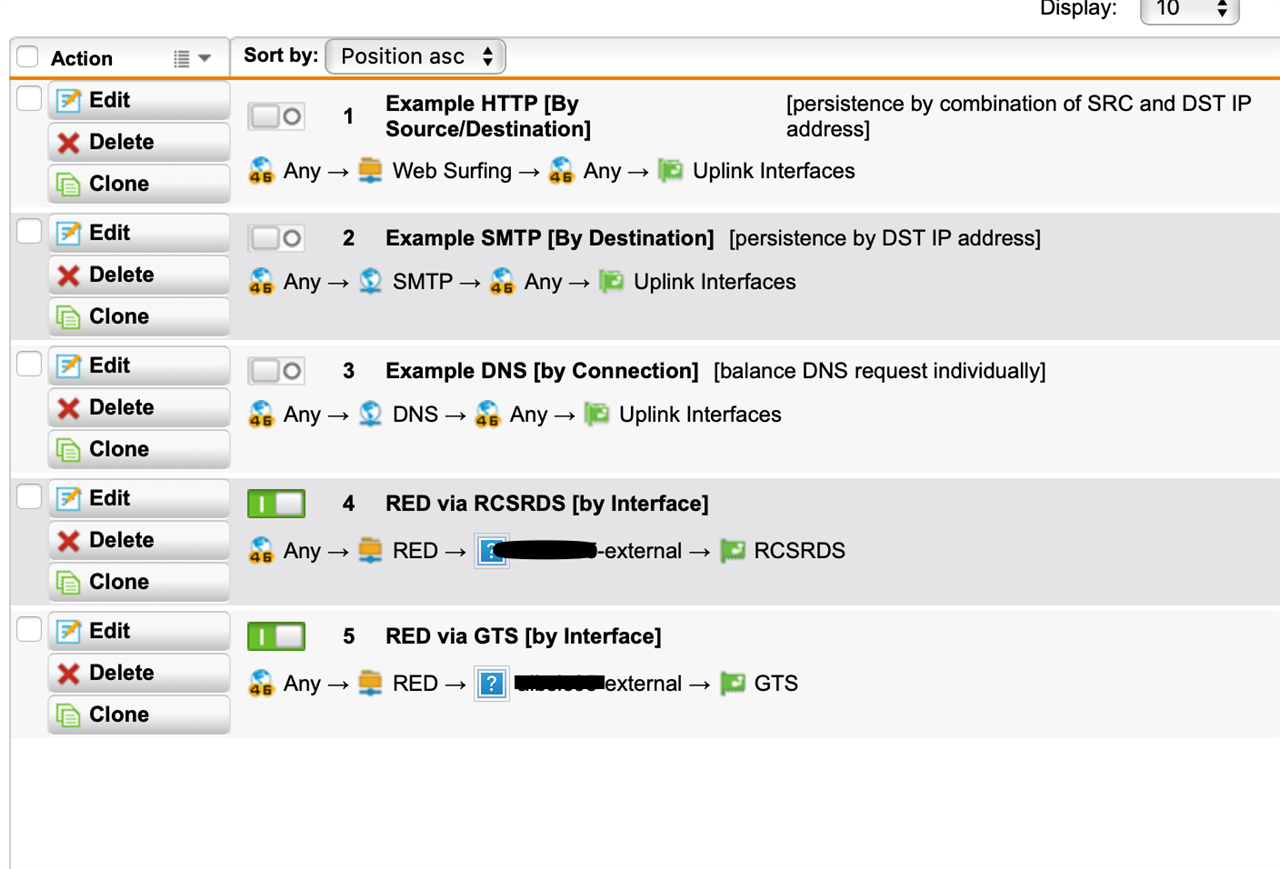
We use UTM2UTM red tunnels for many years and they are working very well. Recently our datacenters have upgraded to multi-homing and with multiple external transfer nets (one for each provider) we would like to have some fail-overs for the RED tunnels. They connect to the external IP address of the UTM, so in case an ISP link goes down the tunnel is also lost. For hardware REDs you can configure a secondary UTM uplink address, which somehow does not exist for UTM2UTM connections.
I tried an availability group, but thats also not supposed as the UTM peer address.
Of course, we could have two tunnels running at all times, one to each ISPs address space and then use OSPF on top of that, but it sounds a bit like overkill.
Any ideas on how that might be possible?
Thank you,
Ronny
This thread was automatically locked due to age.