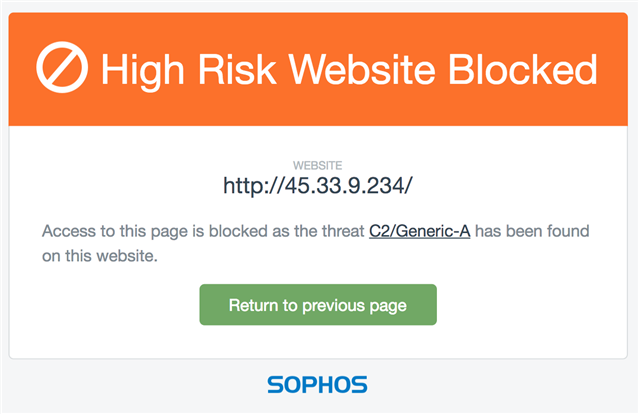
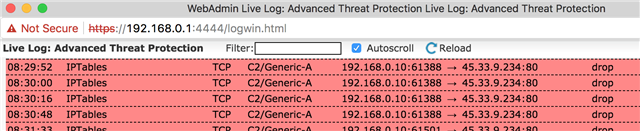
I'm having multiple UTMs reporting a C2/Generic-A from IP address: 45.33.9.234. I have scanned every server/PC that is reporting on and there is never anything there. I believe this is a false positive and I cannot get Sophos to help me out on this one. I've been hung up on twice and all the support reps can tell me is that the PCs are infected and that there's nothing they can do before hanging up.
This thread was automatically locked due to age.