Hi all,
While testing some stuff on travel, I've discovered that my SSL VPN connected client can make DNS requests to ANY dns server (home ISP router, Google public DNS etc).
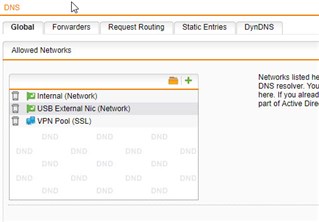
That's a little weird to me because my Network Protection --> Firewall --> Rules are completely exempt of DNS based rules, i rely on my UTM DNS server which forwards requests to my Home ISP router.
I've been under the impression that with no matching rules, traffic should be denied. Am i wrong here?
Also, i've verified from a Home LAN based host via RDP, the LAN hosts have no DNS access to any other DNS server than my UTM dns server. any other attempts at UDP 53 is dropped. The live logs show Default DROP hit for such traffic, although via the SSL VPN it passes through..
Any ideas are welcome.
Cheers,
m.
This thread was automatically locked due to age.