Hi
We have an SG210 running firmware 9.413-4.
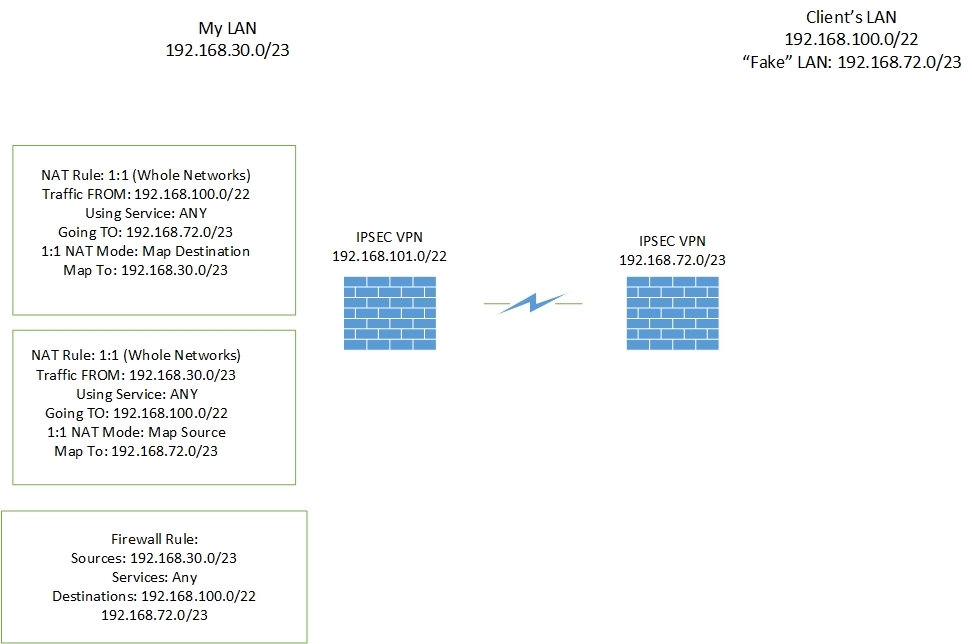
I have a S2S VPN to a client, the client uses the same subnet as ours so I have it NAT'd on my end. It looks like this:
NAT Rule for traffic going from my LAN to my clients LAN:
Rule Type: 1:1 NAT (whole networks)
Matching Condition:
For traffic coming from: My LAN
Using service: Any
Going to: My clients REAL LAN
Action:
1:1 NAT mode: Map Source
Map to: My clients FAKE LAN
NAT Rule for traffic coming from my client's LAN to my LAN:
Rule Type: 1:1 NAT (whole networks)
Matching Condition:
For traffic from: My clients REAL LAN
Using Service: Any
Going to: My clients FAKE LAN
Action:
1:1 NAT mode: Map destination
Map to: My LAN
The VPN terminates on the fake LAN (at the client's end)
The VPN works fine, we can access their system fine aside from one aspect.
They run a payment gateway, when we try to load the payment gateway via browser the connection to the gateway times out. We connect to the payment gateway via a private IP address on their real LAN (via HTTPS)
I can ping this IP address OK. When I enter this address in the browser and monitor the firewall log, I can see that it is being passed by the NAT rule that allows traffic from my LAN to their's. It appears no other firewall rule is used during the process, although I do have firewall rules setup so outbound traffic is allowed to their LAN (including port 443).
The client says they have allowed port 443 via their firewall.
Can anyone think of a reason my setup would cause a timeout when access an IP address on their LAN, or how I can troubleshoot this further?
Many thanks
Paul
This thread was automatically locked due to age.