Dear all,
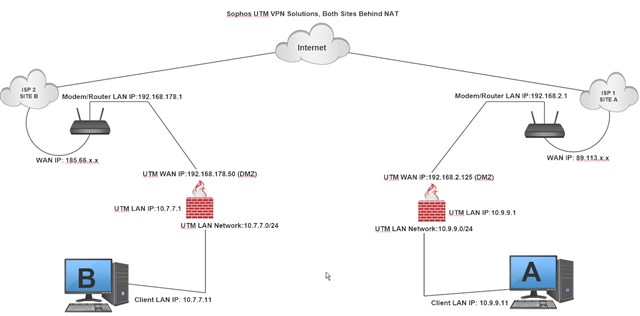
I have two Sophos UTM units at two sites, both are currently behind NAT routers. Both sites have Static Public IPs, both sites use PPPOE to connect to the internet. The PPPOE in both cases is being handled by the NAT router rather than the UTM.
I would like to connect up a site to site network via IPSec using these two UTMs.
Everyone says you have to create a NAT, But I don't know the steps ??
Fowording :
Router NAT : 500TCP/UDP 5400TCP/UDP
Any suggestions on how to solve this? If you need any additional info please do not hesitate to ask.
This thread was automatically locked due to age.

