Intrusion Prevention Alert An intrusion has been detected. The packet has *not* been dropped. If you want to block packets like this one in the future, set the corresponding intrusion protection rule to "drop" in WebAdmin. Be careful not to block legitimate traffic caused by false alerts though. Details about the intrusion alert: Message........: MALWARE-OTHER Win.Malware.Ursu-9821797-0 download attempt Details........: https://www.snort.org/search?query=56912 Time...........: 2021-02-12 02:00:32 Packet dropped.: no Priority.......: high Classification.: A Network Trojan was Detected IP protocol....: 6 (TCP) Source IP address: 184.150.154.11 Source port: 80 (http) Destination IP address: xxx.xx.xx.xxx Destination port: 51576
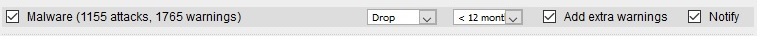
I checked the settings in IPS attack patterns, and all rules are set to "drop"

|
|
|
This thread was automatically locked due to age.