Hello,
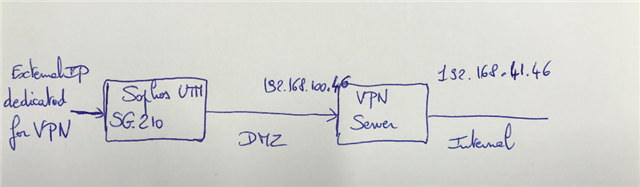
We have a solution VPN enabled with SG-210 UTM working fine with L2TP/Ipsec remote access built-in.
And we have implemented a Microsoft VPN server with Remote Routing Access Role in order to use Microsoft Azure MFA NPS extension fro RADIUS.
--> FYI Radius Test from the FW doesn't work anymore once NPS Extension for MFA installed on the Radius server
-->Reason we have tried to implemented this VPN server enabling the same protocol L2TP
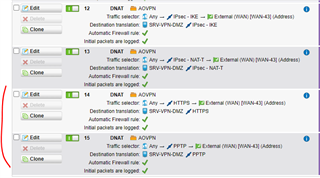
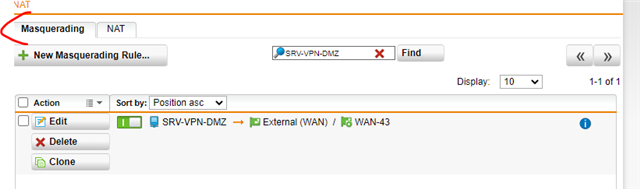
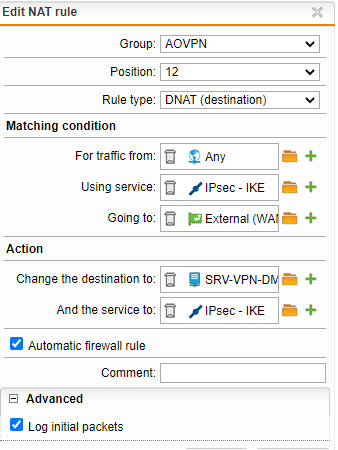
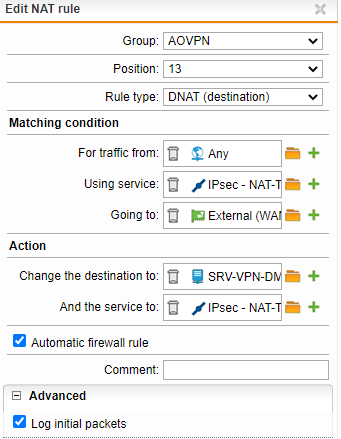
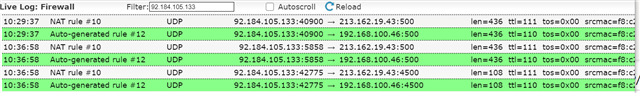
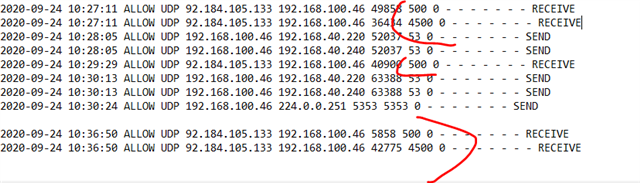
VPN connection works fine with protocol PPTP and PPTP enabling with several DNAT rules configured like below:
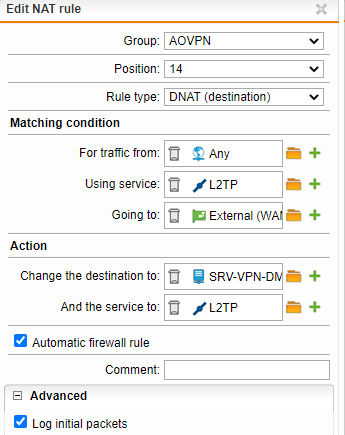
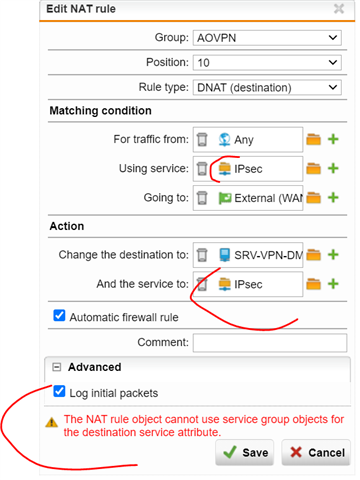
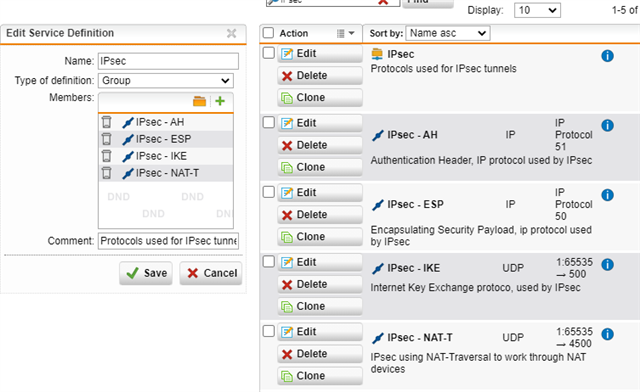
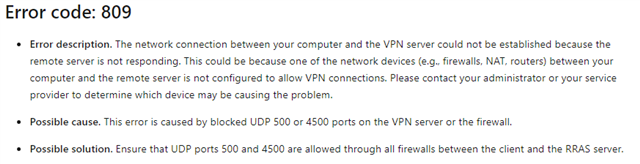
But it doesn't work for L2TP/Ipsec despite several rules attempts: same rule also with L2TP protocol enabled
What are the exact rules to be implement for this protocol so it could run fine?
Is there maybe some restricitons for this model?
Thanks in advance.
Best regards.
Jean-François
This thread was automatically locked due to age.