I have probably the most basic firewall question:
I have 10 interfaces (private subnets) on my UTM. Let's call then 'Internal Network A', 'Internal Network B', Internal Network C', etc.
And I have 1 Internet interface.
In UTM there is a built-in object named "Internet IPv4". As the name implies it seems logical that this object means "access to the Internet"
I create an SNAT rule which allows everything on 'Internal Network A' to be able to access the Internet, over Any port.
Rule works, and users on that internal network can get to the Internet.
But then I discover that Internal Network A also now has access to Internal Network B. Huh? Why is that? OK, so I create a rule that explicitly DENIES access to Int Network B from Int Network A. That doesn't work. Users on A can still access stuff on B.
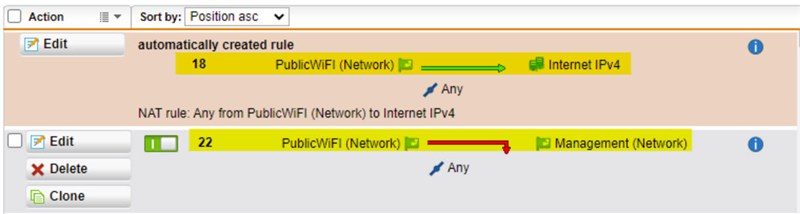
Turns out, when I created the SNAT rule it also created an automatic firewall rule...
Source: Internal Network A
Services: Any
Destinations: Internet IPv4
Which still seems fine. However it appears "Internet IPv4" really means "the Internet plus all other networks".
Is there an object in UTM that really does mean 'Internet Only" that I should have used in my SNAT rule (and consequently in the automatic firewall rule)?
If not then the only option is to:
1. Delete the automatic firewall rule
2. Create a new rule that explicitly blocks traffic from Internal Network A to all other Internal networks
3. Followed by a rule that allows full access from Internal Network A to Internet v4
This thread was automatically locked due to age.