Dear community,
I have a problem making some drop rules working as expected.
It actually drops all protocols (i tried to telnet some random ports, and i can see my drop rule popping in the firewall log) but HTTP/HTTPS
packet blocked:
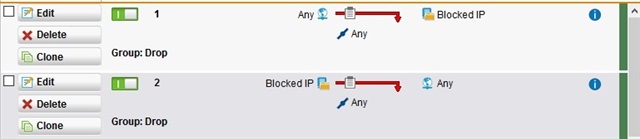
The rules are :
Basically, i've created a network group containing a bunch of forbidden IP addresses. All traffic coming from or going to those destinations must be dropped and the call must be logged in the firewall event log.
A i said, when i try to reach any of those addresses on ports 443/80, packets are not dropped.
We use a transparent proxy managed by the UTM, and the only way to really block the HTTP/HTTPS outgoing access to those IP is to create an object in the blacklist. Absolutely not manageable for hundreds of IP addresses...
Does the transparent proxy bypass the firewall rules concerning HTTP/HTTPS protocol ? It would be quite... unsecure.
How can i prevent reaching those destinations out over this 2 damn ports ?
thank you for your help
This thread was automatically locked due to age.