Hi,
I have installed a new UTM 9.6 a couple of weeks ago and get's a little bit confused about the masquerading setup.
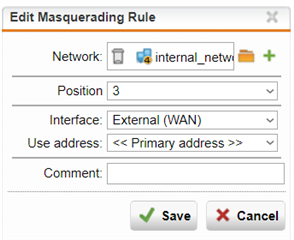
I have set up the masquerading roule internal(LAN)>external(WAN) and service=ANY to allow internal devices unrestricted access to the internet. In addition to this the UTM Online Help states that "Note – You need to allow traffic from the internal network to the Internet in the firewall if you want your clients to access external servers."
This is not necessary in my new UTM. Internet access is granted without creating the firewall rule. Should it work like this???
In the next step I create a firewall roule (at the top) to block internal(LAN)>external(WAN) service=ANY just to see if the internet access is blocked by the firewall. It isn't. Internal devices is still granted internet access through the masquerading roule. Is this behavior be correct???
BR
Mathias Pyk
This thread was automatically locked due to age.