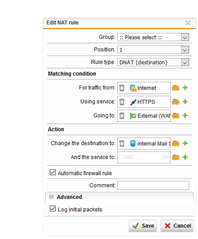
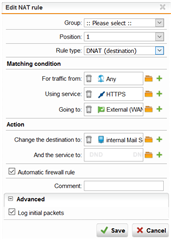
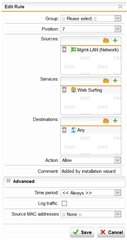
Hello, I have created a DNAT rule (NAT rule #1) for the port https/443 to an internal server. (Traffic from Internet: Internet = Group of Sophos default definition: Internet IPv4 and ...IPv6).
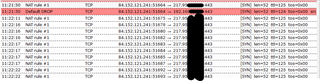
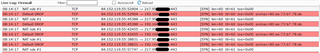
In the firewall log I see that the packets are forwarded. But still in the same moment the packets are droped !??

If I switch the DNAT rule off and on again, then the packets are forwarded without droping?!! Here comes the second crazy thing: The forwarding do his job until the External (WAN) interface connection is re-established after 24 hours. (In Germany, a Internet (VDSL) connection is disconnected every 24 hours.). Then the droping of 443 start again until I do the step I decripted.
I have already checked my other firewall rules, but here I have no rule for port 443/https that could cause the problem.
How can I find out which setting or rule is responsible for the behaviour? I don't want to manually turn the DNAT rule off and on every day :-(
This thread was automatically locked due to age.