I notice when copying files to/from a remote client connected with SSL (openvpn) or l2tp/ipsec top reports high snort cpu.
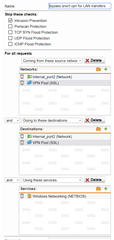
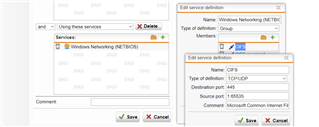
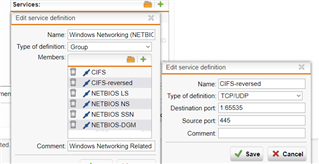
I've been trying to figure out how to properly formulate an exception but have been unsuccessful.
Internal_port2 = local lan (behind utm)
VPN Pool (SSL) = IP pool assigned to openvpn client
I can turn off ips entirely which will disable any snort scans but I'd like to leave it enabled but ignore this type of traffic.
Of course nothing shows up in the ips log because it's not detecting anything intrusive/malicious. Unlike firewall port blocking I've found no way to observe what it's actually scanning so I can apply the proper exception.
Thanks!
This thread was automatically locked due to age.