Hello,
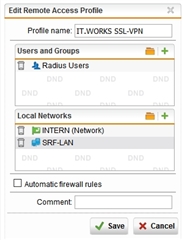
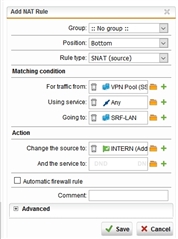
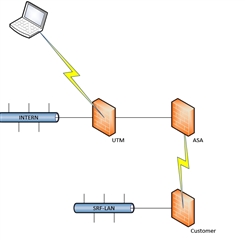
we have in the company a 2nd router (vpn-router) which will only accept connections from our clients network (call it 192.168.1.0/24). I cannot manage that router, it’s preconfigured. Sophos FW manages that network.
If I remote via SSL, I get as usual the vpn pool IP.
In that case, I cannot access the router.
Is there a way that I can have an internal client IP when remoting in? Maybe 1:1 NAT or so?
This thread was automatically locked due to age.