Hello all,
Firstly, I would like thank the Sophos team for providing us with a free UTM Home edition - It is one of the best fully featured FW appliance that is free and I am so impressed by the drag and drop UI.
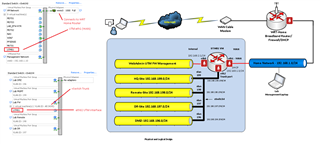
If possible I'm looking to expand the use of the UTM VM appliance to use the ESXi vSwitch Port Groups to create multiple VLANs to simulate typical DMZ scenarios as shown in the attached diagram.
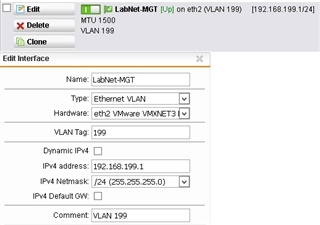
Diagram updated : with the addition of eth2 (third interface) which now connects to the vSwitch trunk port and carries the port group tagged VLANs.
Any help will be greatly appreciated for creating the basic fw rules to enable basic internet access through the WAN port.
This thread was automatically locked due to age.