Hello,
i understand that a similar question has been asked in the very very past but i am still not able to understand it as i lack some understanding of how this works.
I have a virtual appliance at home as the next hop after the router and i also have a VPS (OpenVZ). I would like to create a Site-to-Site VPN between the two. I found and installed OpenSwan on the VPS. In the VPS, using Webmin, i created a new IPSec connection calling it home, using the following settings:
Connection name: Home
Compress data? Default (usually No)
Connection type Tunnel
Authentication method RSA
Perfect forwarding secrecy? Default (usually Yes)
Authentication mode Default (usually ESP)
Keying re-tries Default
ESP algorithm Default (usually MD5)
Accept this ESP algorithm only? No
Connection key lifetime Default
Keying channel lifetime Default
Public IP address {public hostname}
System identifier Default
Private subnet behind system None
When i try to connect to the UTM from the VPS, i get the following error:
000 initiating all conns with alias='home'
021 no connection named "home"
To do the setup on the UTM, i did create a remote gateway:
Gateway type: initiate connection
Gateway: (the ip address of the VPS)
Aythenticaiton type: RSA key
VPN ID type: IP Address
VPN ID: {the ip address of the VPS)
Remote networks: Any
and then i created the connection:
Remote gateway: VPS
Local interface: External
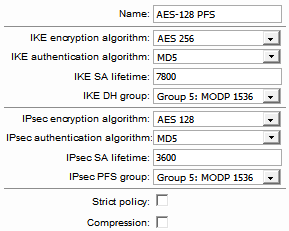
Policy: AES-128 (i know this is wrong, but i tried the others and none worked)
Local Networks: Internal
Automatic firewall rules: Yes
But of course it is not connecting.
Any ideas what am i doing wrong?
Thanks!
This thread was automatically locked due to age.