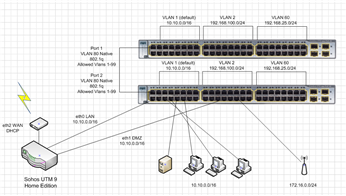
I am new to Sophos and I have the latest UTM home free edition. I have somewhat of a complex home network, and I want to setup VLAN control on the firewall. Below is a drawing of my cisco switch (3950 Layer 3) and it's associated vlans and connections. I am using trunking and allowing all vlans to pass through the two trunk ports (1 and 2), and ports 1 on both switches are connected with a standard ethernet cable. I have tried connecting the other trunk port (2) carrying all of the VLANS to "eth0" of my UTM and I lose all connectivity when I do so. I'm not sure what to do as I can't find much information on how to achieve this. I see where to add the subinterfaces to "eth0" of the type VLAN in the management gui, but I"m not sure what to do here. I'm also attaching my VLAN config on the router below. Any direction on how to achieve this would be awesome.
Thanks,
FYI...The trunk ports are working properly between the switches, and I have connectivity between all vlans on both switches.
---------VLANS-------------------------------------------------------
VLAN1 Default (10.10.0.0/16)
VLAN2 DMZ (192.168.100.0/24)
VLAN50 Data ()
VLAN60 Subnet 1 (192.168.25.0/24)
VLAN99 Management (10.9.0.0/16) (Port 16 on both Switches)
-----------------Cisco Configs------------------------------------------------------------
SW2#show vlan
VLAN Name Status Ports
---- -------------------------------- --------- -------------------------------
1 default active Fa1/0/3, Fa1/0/4, Fa1/0/5, Fa1/0/6, Fa1/0/7, Fa1/0/8, Fa1/0/9, Fa1/0/10, Fa1/0/11, Fa1/0/12, Fa1/0/13, Fa1/0/14, Fa1/0/15, Gi1/0/1
Gi1/0/2, Gi1/0/3, Gi1/0/4
2 DMZ active Fa1/0/17, Fa1/0/18, Fa1/0/19, Fa1/0/20, Fa1/0/21, Fa1/0/22, Fa1/0/23, Fa1/0/24, Fa1/0/25, Fa1/0/26, Fa1/0/27, Fa1/0/28, Fa1/0/29
Fa1/0/30, Fa1/0/31, Fa1/0/32
50 Data active
60 Subnet1 active Fa1/0/33, Fa1/0/34, Fa1/0/35, Fa1/0/36, Fa1/0/37, Fa1/0/38, Fa1/0/39, Fa1/0/40, Fa1/0/41, Fa1/0/42, Fa1/0/43, Fa1/0/44, Fa1/0/45
Fa1/0/46, Fa1/0/47, Fa1/0/48
80 Native active
99 Management active Fa1/0/16
1002 fddi-default act/unsup
1003 token-ring-default act/unsup
1004 fddinet-default act/unsup
1005 trnet-default act/unsup
------------------------------------------------------------------------------------
Show Interfaces Trunk
Port Mode Encapsulation Status Native vlan
Fa1/0/1 on 802.1q trunking 80
Fa1/0/2 on 802.1q trunking 80
Port Vlans allowed on trunk
Fa1/0/1 1-99
Fa1/0/2 1-99
Port Vlans allowed and active in management domain
Fa1/0/1 1-2,50,60,80,99
Fa1/0/2 1-2,50,60,80,99
Port Vlans in spanning tree forwarding state and not pruned
Fa1/0/1 none
Fa1/0/2 1-2,50,60,80,99
----------------------------------------------------------------------------------
This thread was automatically locked due to age.