Hi there,
maybe the answer to my questions is quite obvious and I just don't see the forest for the trees...
But I currently don't have a clue and I don't even know how to search for the answer.
So please also bear with me if the question was already answered thousands of times and I didn't find it.
My provider provides me with an IPv6 network 2001:db8:1::/48.
My Sophos UTM has the IP address 2001:db8:1::2 on its Internet interface (eth0). The provider's endpoint has the address 2001:db8:1::1.
From an IPv6-enabled host in the Internet, I am able to reach both 2001:db8:1::1 and 2001:db8:1::2. So far so good.
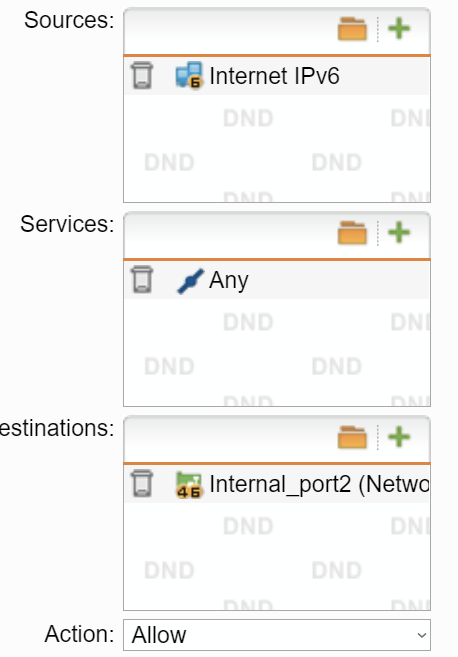
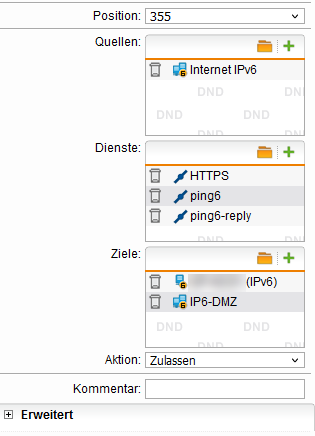
As this is a very large network, I would like to split it up into several smaller ones. I am unsure how to accomplish that. (My provider did not delegate a separate subnet which I could use...)
So I thought, I assign the network 2001:db8:1:100::/64 to eth1 with eth1 having the IP address 2001:db8:1:100::1 and a client in that network having 2001:db8:1:100::2.
I thought, the UTM should receive all the network packets for the /48 subnet and it can decide to which interface the packets are to be forwarded to, i.e. all packets in the network 2001:db8:1:100::/64 should be forwarded to eth1, as the firewall knows this subnet. (Although now, there are two network interfaces in the same network - at least as eth0 understands the networks. The eth1's address (and whole address space) is in the same network where also eth0's IP address lies... So somehow, this seems wrong...)
I cannot reach either 2001:db8:1:100::1 or 2001:db8:1:100::2. Does anyone have an idea what I am doing wrong?
Or isn't that possible at all with the IP address and subnet given from my provider? (But why does my provider give me a /48 network, then?)
Any help would be highly appreciated.
Best regards
Tom
This thread was automatically locked due to age.