I have two UTM VMs running as a high-availability pair. I need to check something on the slave/standby node, so I'm attempting to SSH to it by means of the ha_utils ssh command from the master/active node. I'm SSH'd in to the master as root using an ssh key, but when I try to connect to the slave I get Permission Denied.
<M> astaro:/root # ha_daemon -c status
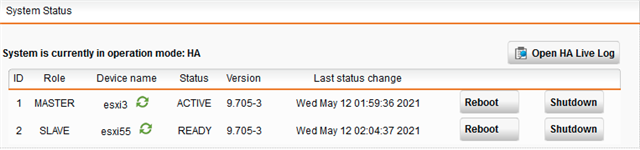
Current mode: HA MASTER with id 1 in state ACTIVE
-- Nodes -----------------------------------------------------------------------
MASTER: 1 esxi3 198.19.250.1 9.705003 ACTIVE since Mon May 10 10:26:56 2021
SLAVE: 2 esxi55 198.19.250.2 9.705003 ACTIVE since Mon May 10 10:31:57 2021
-- Load ------------------------------------------------------------------------
Node 1: [1m] 0.00 [5m] 0.01 [15m] 0.05
Node 2: [1m] 0.01 [5m] 0.02 [15m] 0.05
<M> astaro:/root # ha_utils ssh
Connecting to slave 198.19.250.2
loginuser@198.19.250.2's password:
Permission denied, please try again.
loginuser@198.19.250.2's password:
<M> astaro:/root #
I know I'm using the correct password for loginuser - I've even changed it via the web UI to be sure I wasn't misremembering, but to no avail.
Any thoughts or suggestions welcomed. Thanks!
This thread was automatically locked due to age.