First of all, thank you for your patience as I am new to the Sophos UTM world.
We have a Sophos UTM 9 that is making an IPsec connection to a customer's network. We need to NAT a single IP on our local end of the connection to avoid an IP conflict on their end. Here are some details.
The remote Gateway has been defined as well as a few remote networks
10.3.1.0/24
10.3.2.0/24
10.4.0.0/16
Our local interface is in place and our local network has been configured
192.168.110.0/24 (This network does not exist in our environment and is where the NAT comes into play)
Keys shared, policies match, the SA's establish without problems.
Now,
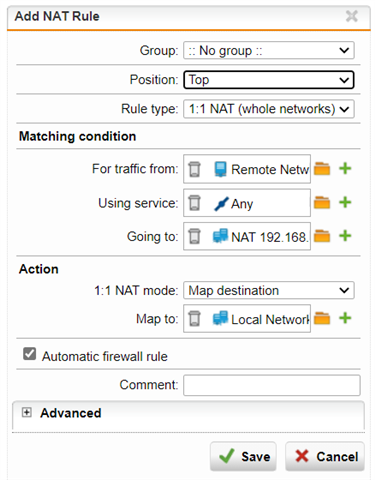
What I'm trying to do is NAT 192.168.110.10/32 (does not exist) to our actual server interface with an IP of 10.200.110.10
I've tried creating a DNAT, a DNAT and a SNAT, a 1:1 NAT. I've tried creating an interface for 192.168.110.10 (which actually will respond to a ping from the customer's side) and setting up the NAT using that interface as opposed to network, but I cannot get any communication from their remote networks to our 10.200.110.10 server. Automatically created firewall rules have been used in every scenario. The logs don't seem to show any ICMP traffic at all when I'm testing (i've heard that's just a "Sophos thing" and it's not possible to do??). I've tried instruction from another post here to view a tcpdump but the results come out unreadable (i think resolving this will be my next step going forward). Is there static routing that's required for this? I figured the VPN would handle that.
I'm sure I'm just missing something dumb since I'm not familiar with the WebAdmin interface. It seems straightforward enough but I sure can't get it to work.
Any insights would be greatly appreciated.
Thanks!
This thread was automatically locked due to age.