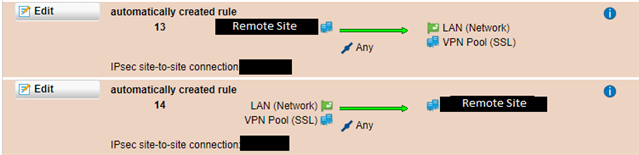
I have recently aquired a sophos firewall at work and I have successfully created a IPSec tunnel with a remote site ( IPSec Site-to-Site ) that is attached to our LAN network.
( Users can connect to this remote site via the LAN network flawlessly )
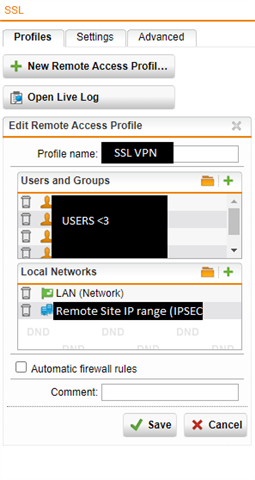
After the pandemic, most of the users are remote working and now using a VPN SSL connection ( which I assigned them to a different IP addrerss pool ) to connect to the LAN network and use a printer or other any other local servers.
My boss has asked me to allow these remote working users to access the previously mentioned remote site that are using the VPN SSL.
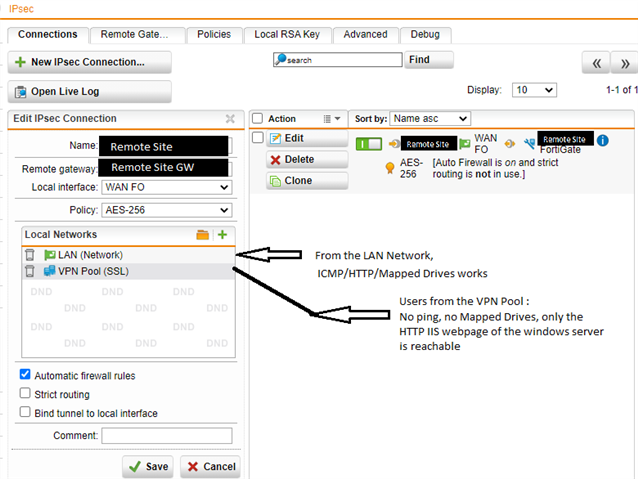
So, I added the VPN SSL network with automatic firewall rules under the "Local Networks" in the IPSec Site-to-Site VPN and added the VPN SSL network in the remote site firewall as well.
I can access the remote site's IIS7 webpage but can't ping nor see it's network mapped drives.
My guess is that there is a firewall rule or a filter that is messing up something.
I looked into some older forums/answers that mentions SNAT,
Can anyone help me?
Thanks!!
Edit- The Sophos Firewall is a UTM 9
This thread was automatically locked due to age.