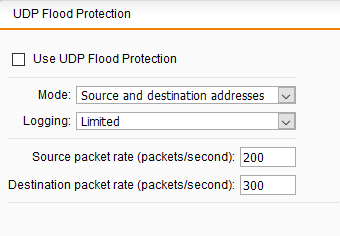
Hi folks,
I am struggeling with iOS devices (iOS 14) behind a Sophos UTM Firewall using Firmware 9.705-3. The UTM is using Firewall Rules, Intrusion Prevention and Endpoint Protection features. Instagram stories, IGTV videos and Facebook videos are buffering all the time once the devices are behind the Sophos UTM and I don't know what's the problem...
I tested it without the UTM going directly to the router and it's working fine. Therefore somethings not right within the UTM. LiveLogs are fine, traffic won't be blocked on the devices. Please help, it's just annoying and I can't figure out what's going on...
All other streaming services like YouTube, Netflix, Amazon Prime Video are working fine on the iOS devices...
BR,
fl4m1ngh0m3r
This thread was automatically locked due to age.