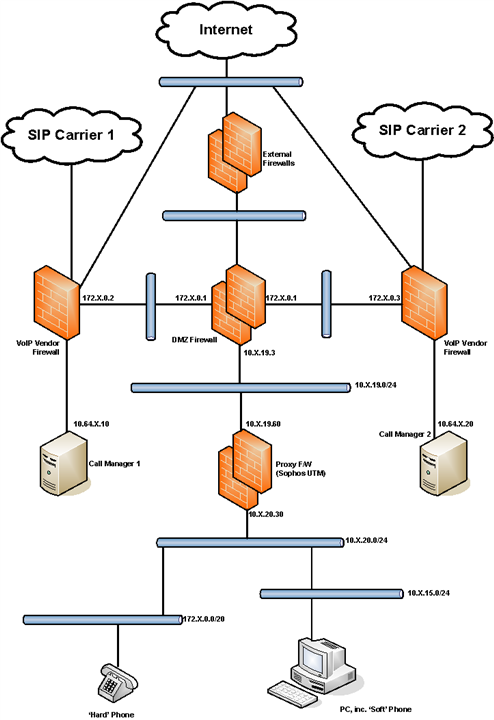
Hi folks,
We have a pair of SG450 Hardware Appliances (Hot-Standby Mode) running UTM Version 9.703-3 acting as Web Proxy Firewalls at the edge of our internal network.
Up until now we have been using Masquerading as the preferred method of hiding internal network IP Addresses.
However, we are in the process of deploying a new VoIP solution which requires that certain traffic does not undergo NAT as it passes through the UTM on it's way to a Call Manager appliance in our DMZ.
For 'hard' phones, i.e. those on a separate internal VLAN of their own, I don't see any issue. Simply create a 'No NAT' rule on the UTM for this particular IP Address range and route it through to the Call Manager.
As for 'soft' phones, i.e. those using the IP Address of the host PC, I'm a little bit confused. If I create another 'No NAT' rule from the internal VLAN of the host PC to a specific destination in our DMZ, i.e. the Call Manager appliance, will the Masquerading rule still apply for all other Internet-bound traffic?
Am I looking at dispensing with Masquerading altogether and instead creating a SNAT rule for general Internet-bound traffic from our internal network as well as a 'No NAT' rule for traffic destined for the Call Manager?
I hope I have explained this okay and look forward to any comments/suggestions.
Many thanks,
John P
This thread was automatically locked due to age.