I'm trying to get utm to pass a dhcp offer and ack through a bridge consisting of 2 interfaces.
eth0 - leg 1 of bridge
eth1 - leg 2 of bridge
eth2 - management interface to for webadmin
eth0/eth1 interfaces are bridged with no ip defined (0.0.0.0/0)
eth0 connects to an upstream dhcp server
eth1 connects to a downstream client configured for dhcp
tcpdump -i br0 port 67 or port 68 -e -n -vv
Executing on dhcp server indicates the following repeating pattern:
|
21:44:43.720005 00:0c:29:2f:65:22 > ff:ff:ff:ff:ff:ff, ethertype IPv4 (0x0800), length 342: (tos 0x0, ttl 64, id 0, offset 0, flags [none], proto UDP (17), length 328) |
From this I understand the dhcp server is receiving the request and making an offer. However, the offer is not getting passed through to the client.
Dhcp relay is configured as follows; 10.10.1.1 is the upstream dhcp server. Bridge interface is the bridge of eth0 & eth1.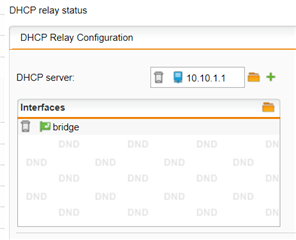
Firewall rule bridge (network) -> any -> bridge (network). Is enabled w/logging. Nothing shows up in the firewall log about blocking the dhcp server reply.
How do get the dhcp server reply traffic to traverse the bridge?
This thread was automatically locked due to age.

