I have successfully followed the instructions in the following link - https://community.sophos.com/kb/en-us/127030.
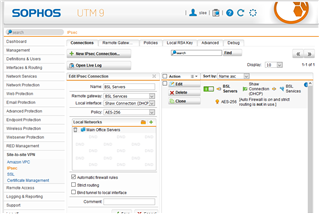
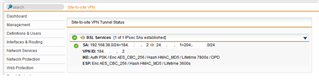
I have an indicator in the Site-to-site VPN page where Test IPsec Tunnel B indicates "1 of 1 IPsec SAs established" on the initiator and Test IPsec A with the same message showing.
Unfortunately, I cannot ping or remote desktop to any of my computers on the remote network. When I use the Sophos SSL VPN client, I am able to remote desktop to the desired systems.
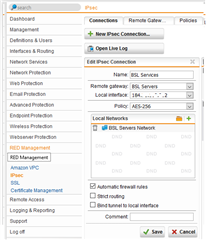
The status of the end points show the following:
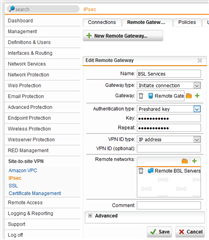
Test IPSec A: 192.168.xx1.0/24=EXTERNAL_IP_1 <-> EXTERNAL_IP_2=192.168.xx2.0/24
VPN ID: EXTERNAL_IP_1
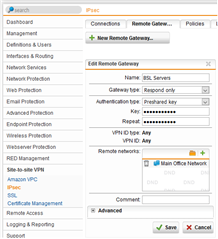
Test IPsec Tunnel B: 192.168.xx2.0/24=EXTERNAL_IP2 <-> EXTERNAL_IP_1= 192.168.xx1.0/24
VPN ID: EXTERNAL_IP_2
Any suggestions will be appreciated.
This thread was automatically locked due to age.