Hi,
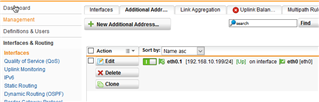
I am using UTM 9 with a single network adapter in order to redirect my traffic based or the host header. Everything works fine, but now I wan to configure the SSL VPN and the User Portal. Since 443 is already used on the Sophos adapter I have created a virtual one with a different IP address to bind to in order to use the VPN and portal on 443.
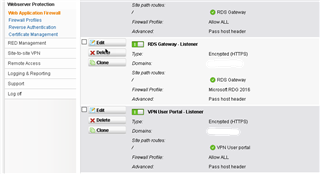
From the internal network the portal and VPN works fine since its hitting the VIP directly, but from outside I can't get the portal to work, I don't know about the VPN yet. I have created a Virtual Web Server that redirects traffic to the "Real Web Server", the VIP of the network interface, again, based on the host header it gets from the browser. Looks like is having trouble redirecting to one of its own IPs.
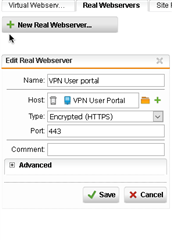
For the real server option I have created a new host and added the VIP of the UTM network adapter.
Can I redirect Web traffic to Sophos own IPs using a Virtual Server?
Thanks
This thread was automatically locked due to age.