Hello, i have been trying to isolate two networks.
Internal=192.168.0.0/24
Public=192.168.99.0/24
I have external DHCP server on 192.168.0.2
There are two scopes for those networks,which are combined into superscope (from what i understood VLAN is better solution).
The problem is that i can't isolate these two networks.
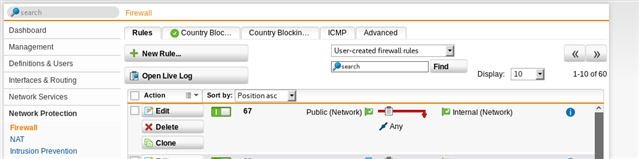
I have tried to create firewall rule to isolate two networks which was unsuccessful.
Also i have tried to prevent public network from accessing internal network when by using the web proxy.
-----------------
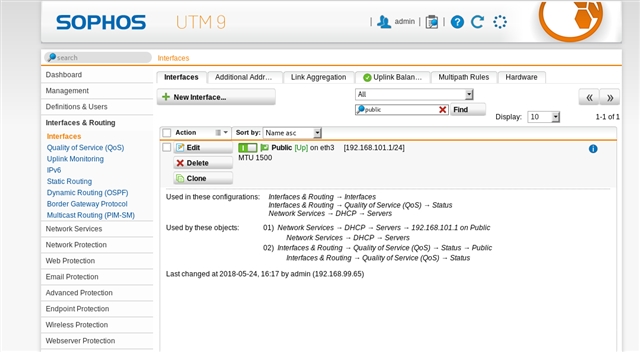
After that i tried to create another network Public2=192.168.101.0/24 on separate interface in sophos (sophos was acting as dhcp server)
And still i wasn't able to separate two networks.
What bothers me most is that sophos doesn't log the connections between the networks.
Any help would be greatly appreciated.
This thread was automatically locked due to age.