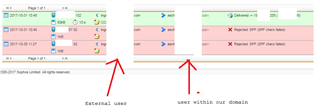
I have received a complaint that an email hasn't been replied to and according to a user within our company he didn't receive it.
after checking from the mail manager there were 3 emails from same person on different dates one of them passed and the others got rejected due to SPF check failed.
Any ideas ?
This thread was automatically locked due to age.