Hi, I have several UTM 9 at different customers. I am not a network specialist though.
I now have a customer in Denmark that needs a different configuration.
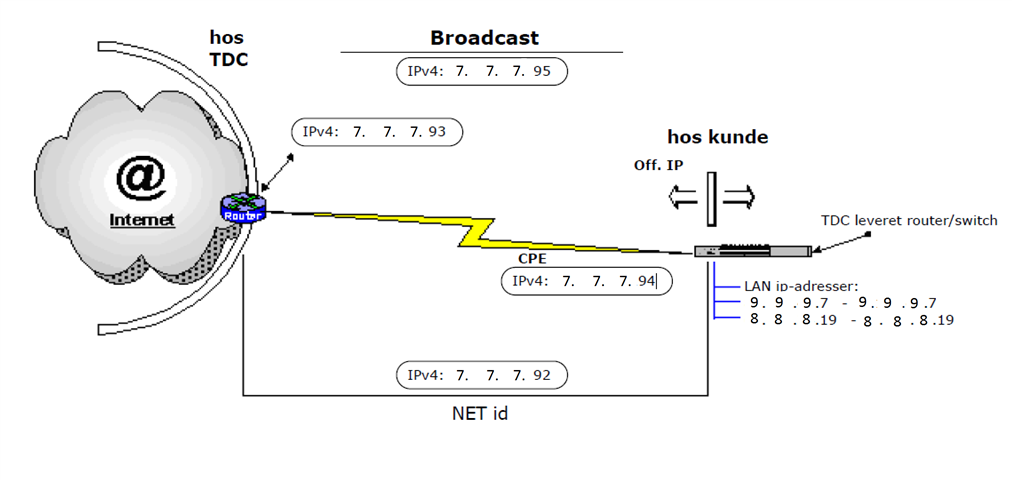
This is the paper TDC in Denmark has sent. I have changed the IP adresses a little though. The thing is that I do not have the router/Switch from TDC. Instead there is an UTM9 there with the WAN-IP 7.7.7.94 and default gateway 7.7.7.93.
I now have a second firewall that is preconfigured, and I can not do any changes to it. It has the adress: 8.8.8.19, and the Default Gateway 8.8.8.18. This is the correct Default GW according to TDC.
TDC in Denmark says that it is pretty easy to configure most Gateways so that I could use the new firewall with adress 8.8.8.19 on one of the Ethernet-ports. They said that I could create a DMZ for this.
Is this the right way? Or how would you have configured it? If possible I would like a step by step instruction, since I do not really know how to proceed.. :)
Best Regards
Andreas
This thread was automatically locked due to age.