Hi all!
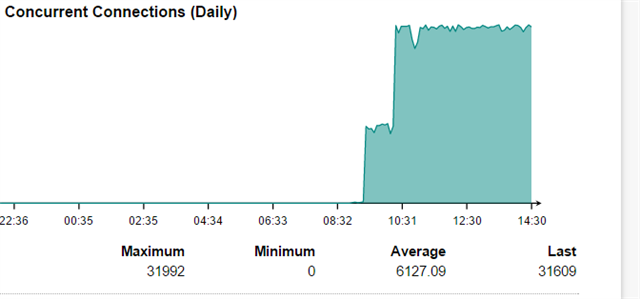
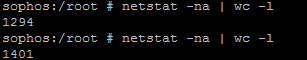
I am using Sophos UTM Home edition v9.408 (which is free) with just about 10 users. The concurrent connections reach the limit 32k immediately after that. Checking in ssh shell with "netstat -na | wc -l" shows only 1k4.
Please show me which one is right and if it is actually 32k, how can I drop it.
Any idea would be appreciated!
This thread was automatically locked due to age.