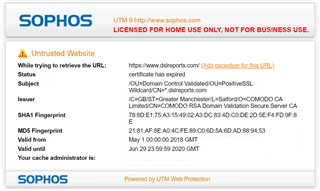
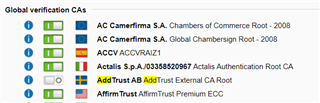
This started this morning (5/30).
Example site
I'm not sure what has expired as the cert is good through the end of June. Both utm and client pc date is accurate. Thoughts?
Edit: Here's the lines from the proxy log.
2020:05:30-12:11:31 utm httpproxy[6727]: id="0002" severity="info" sys="SecureWeb" sub="http" name="web request blocked" action="block" method="CONNECT" srcip="10.10.5.100" dstip="64.91.255.98" user="" group="" ad_domain="" statuscode="502" cached="0" profile="REF_DefaultHTTPProfile (Default Web Filter Profile)" filteraction="REF_DefaultHTTPCFFAction (Default content filter action)" size="3883" request="0xd32d5800" url="https://www.dslreports.com/" referer="" error="Failed to verify server certificate" authtime="0" dnstime="2" aptptime="66" cattime="71" avscantime="0" fullreqtime="242853" device="0" auth="0" ua="" exceptions="patience" category="165" reputation="neutral" categoryname="Technical/Business Forums" country="United States"
2020:05:30-12:11:32 utm httpproxy[6727]: id="0002" severity="info" sys="SecureWeb" sub="http" name="web request blocked" action="block" method="CONNECT" srcip="10.10.5.100" dstip="64.91.255.98" user="" group="" ad_domain="" statuscode="502" cached="0" profile="REF_DefaultHTTPProfile (Default Web Filter Profile)" filteraction="REF_DefaultHTTPCFFAction (Default content filter action)" size="3883" request="0xd4979c00" url="https://www.dslreports.com/" referer="" error="Failed to verify server certificate" authtime="0" dnstime="3" aptptime="67" cattime="68" avscantime="0" fullreqtime="243232" device="0" auth="0" ua="" exceptions="patience" category="165" reputation="neutral" categoryname="Technical/Business Forums" country="United States"
Edit2:
Looks like this is not a utm issue but rather poorly implemented certs?
Edit3: Maybe this is a utm issue as it's not following the cert chain properly?
This thread was automatically locked due to age.