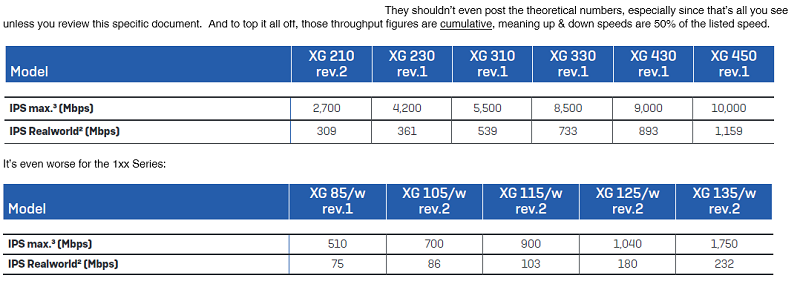
For the record, this is false advertising:
So now I've got to build my own box, and my only Sophos-approved point of reference is a hardware compatibility PDF that was last updated in Sept 2015. The alternative I'm looking at is the SG 210 rev.3, and I'll be paying well over $1k for a device with a 2-core, 2-thread, 2 1/2 year-old $40 CPU. What am I supposed to do?
This thread was automatically locked due to age.