Hello everyone,
I am using the latest version of Sophos UTM and everything is working very well so far.
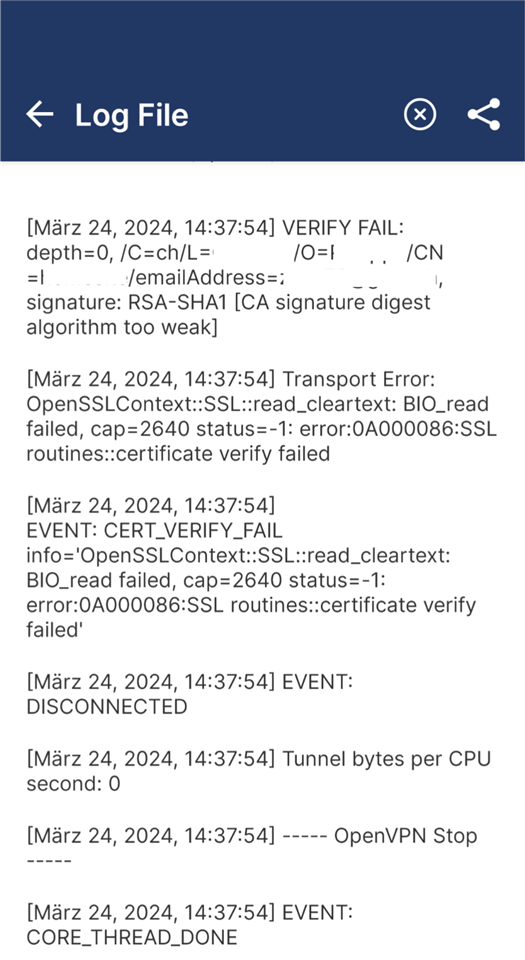
Recently I have the problem that I can no longer create an SSL VPN. I work with a SelfSigned Certificate, I have also tried to create a new one with higher encryption, but the problem persists. Do I have to buy a offiicial certificate so that I can use SSL VPN again?
Error Log can be found in the attachment.
Thanks for your help.
Best regards
This thread was automatically locked due to age.


