Hi Sophos,
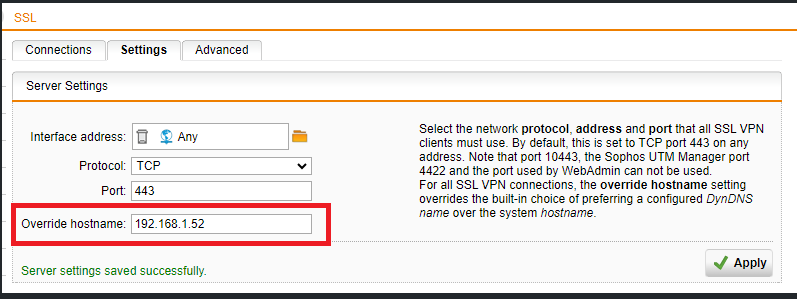
Do you have any information on all your products to the TunnelCrack VPN vulnerability? ref: tunnelcrack.mathyvanhoef.com/details.html CVE numbers CVE-2023-36672. CVE-2023-35838. CVE-2023-36673 CVE-2023-36671
quick summary: two vulnerabilities are listed: Local traffic can be leaked in plain text, IP of VPN server can be spoofed.
Regards
Damien
This thread was automatically locked due to age.