Hi,
I've configured and seviced many UTMs in the past 10 years but somehow I'm stuck now...
Yesterday my workmate asked my why connections to a IIS webserver from a customer are not shown in the logs. I tried some analysis and can't find the problem....
The IIS is only reachable from our external IP for certificate checking reasons. So there is a NAT rule (webserver protection is not activated):
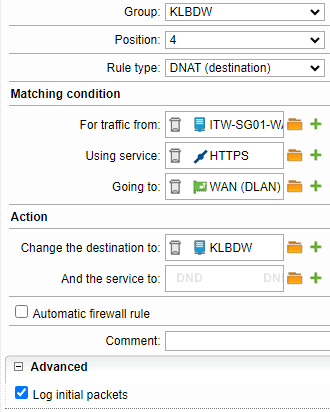
So far, so good. And there is a firewall rule, too.
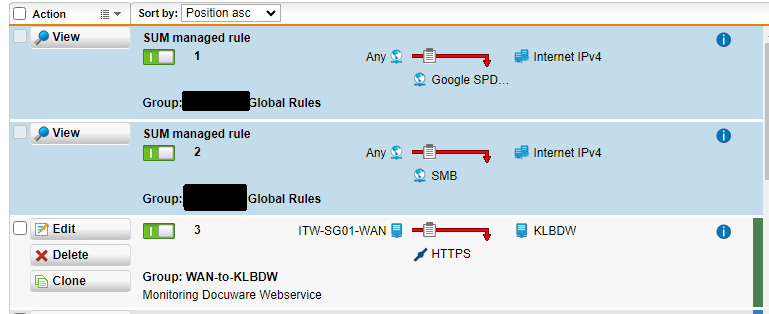
Here it is configured as DROP rule for troubleshooting purposes. As you can see no rule above is "oversteering" that specific traffic. All definitions in both rules are host definitions, not bound to a specific interface (<< Any >>).
From the above two rules I would have expected, that opening the https website on "KLBDW" from our location should not work. But it does! I can open the website without any issues!
I can see the log entry for the NAT rule in the log, but no entry for the firewall rule.
2023:06:15-10:29:43 klb-sg01 ulogd[6228]: id="2000" severity="info" sys="SecureNet" sub="packetfilter" name="Packet logged" action="log" fwrule="62004" initf="eth1" srcmac="..." dstmac="..." srcip="<our public IP>" dstip="<external - prenat IP>" proto="6" length="52" tos="0x02" prec="0x00" ttl="123" srcport="5881" dstport="443" tcpflags="SYN"
If I turn off the NAT rule, it doesn't work - as expected.
But why is it working with a DROP firewall rule?
Were there any changes to the NAT behavior that I missed out (like automatic allow)?
This thread was automatically locked due to age.
