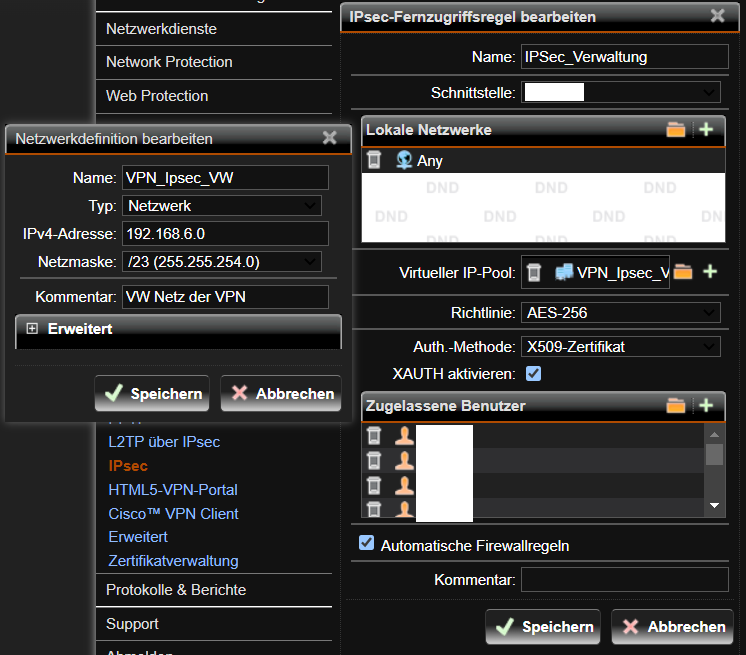
The Problem was first described here : Remote Access via IPSec, Client connected but not receiving packets
Currently running Version 9.713-19 of the Sophos UTM 9 SG550 Firewall.
Client IPSec version is the latest available : 2.2.75
NAT-Traversal Keep Alive has since been changed to 10 seconds.
Once the Client is connected via the VPN it can ping the Firewall successfully.
Network Protection rules must be fine since other users have no Problems whatsoever.
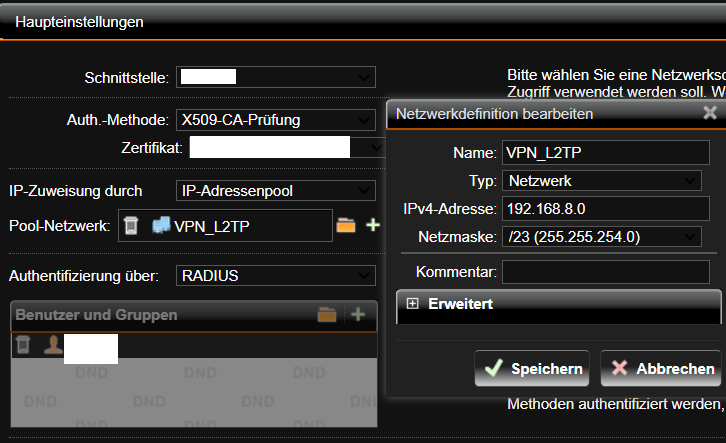
We also use L2TP over IPSec as VPN and that stopped working as of late aswell.
The VPN on Sophos is simply not reliable, some users can't connect on either of the VPN solutions and I have wasted so much time already looking for solutions.
This thread was automatically locked due to age.