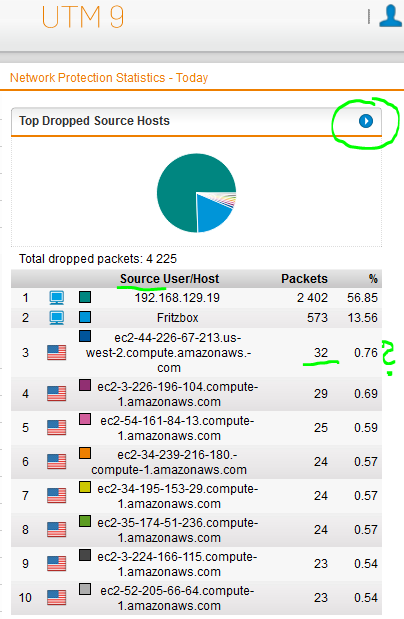
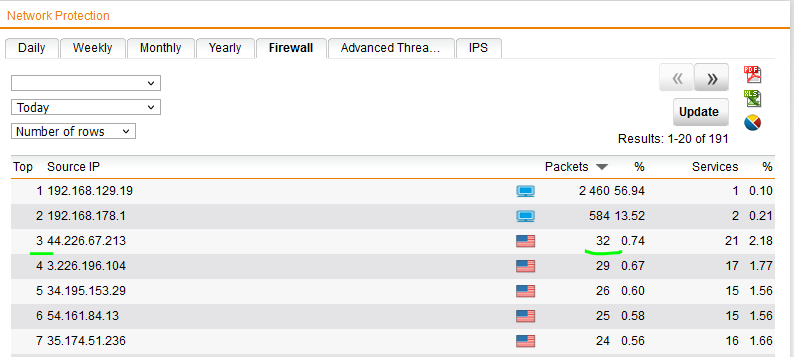
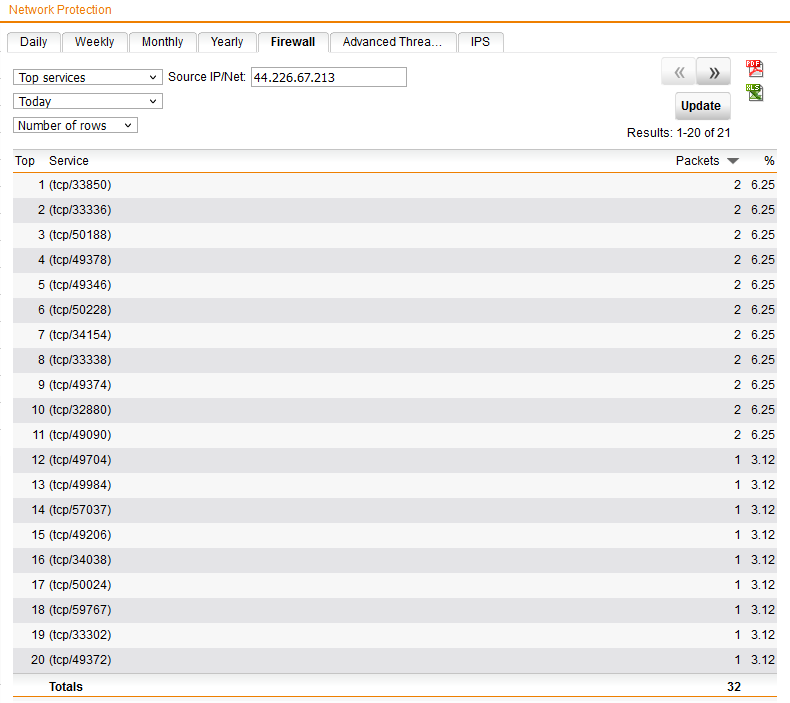
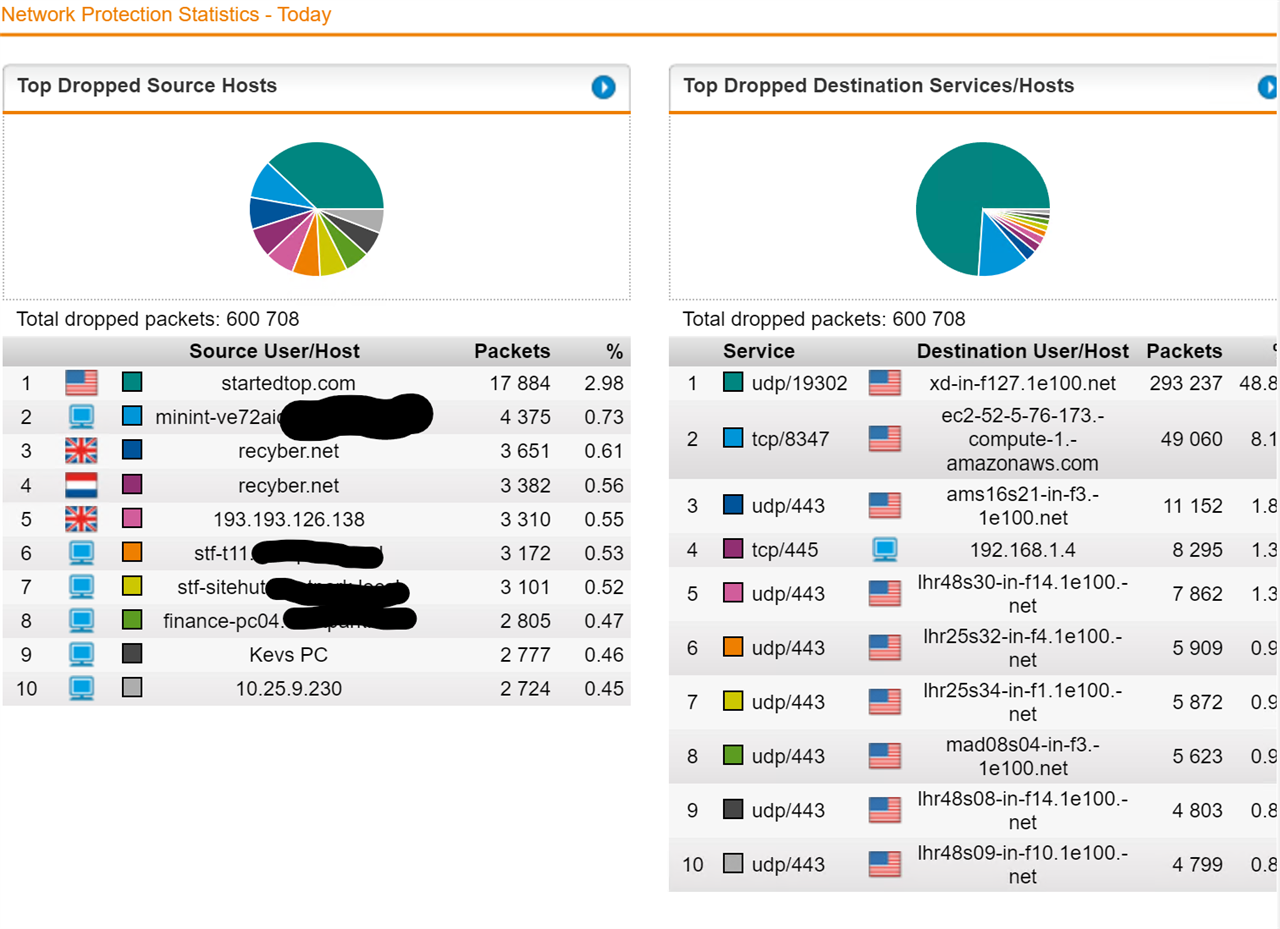
so this my stats from the UTM
how do I find out if these are from within the network going outwards i'm just worried that there could be something going off that needs my attention, we block alot of ad web traffic as we don't allow staff to click on ad links but that's by the by BUT just wondering how i could find out where e.g the request for startedtop.com is coming from or could it be that when browse the web whatever server the site is hosted on our firewall is blocking it ?
This thread was automatically locked due to age.