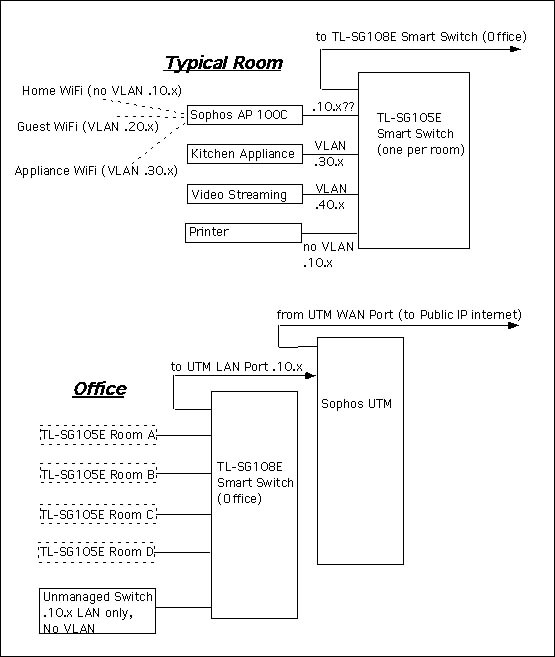
I would like to segment my network into multiple LANs and VLANs.
Right now, I have one happy LAN network, all shared with all devices. Small unmanaged switches in each room, converging to a large 24 port unmanaged switch in the office:
- Primary real LAN in the LAN port of the Sophos UTM - 192.168.10.x /24
- Wireless network SSID 1, bridged to LAN - 192.168.10.x /24 ... too.
Future:
- Existing LAN and SSID 1 Wireless on that same LAN for servers, personal computers, printers, etc. 192.168.10.x /24
- New segmented networks with internet access through the firewall, but isolated and blocked from the LAN above:
- Guest wireless network on separate SSID 2 192.168.20.x /24
- New virtual network VLAN 10 for home appliances (kitchen oven, sump pump, etc.), some on Ethernet, some on Wireless with its own SSID 3 (... .30.x /24)
- New virtual network VLAN 20 for streaming devices (TiVo, Roku, AppleTV, etc.), some on Ethernet, some on Wireless with its own SSID 4 (... .40.x /24)
- New virtual network VLAN 30 for cameras (... .50.x /24)
- You get the idea...
Each room has a single Ethernet port. The ethernet cables converge in the office closet. Currently each room has a small 5 port switch. A room may have any combination of Sophos AP 100C, devices that belong on the 192.168.10.x LAN (computers, printers, servers), and various ethernet and wireless home appliances, streaming devices, etc.
In other words, a given room may have a combination of different devices, each one associated with a different network segment / VLAN. At the same time, the same VLAN network segment may have devices in different rooms.
I ordered managed 5 port switches (L2, 802.1q) to replace the unmanaged switches in the rooms. I ordered an extra managed 8 port switch for the office closet. I am not sure I need it. (To the best of my knowledge, the 24 port unmanaged switch will not pass tagged VLAN Ethernet packets.)
-> Am I on the right track? Is there a better way to segment my network?
-> Do I have what I need to make this work?
-> What is the best way to configure these devices to segment my network as described?
P.S. Can I configure the new network segments to be IPv4-only, but leave my primary LAN IPv4 and IPv6?
This thread was automatically locked due to age.