Hello all,
Your friendly neighbourhood networking newb here. I'm attempting to avoid going through another 18 hours of no internet at head office (yay for nation wide outages) knocking out the other remote offices. I know that REDs can't fail over to another UTM (unfortunately); however, I did come across Manual / split mode when digging into options. This may all be temporary, I hope, as I'm closer to convincing the execs for a secondary fibre provider and as our present connections with UTMs in place will be upgrading to 1Gbps. I'm sourcing new UTMs (probably SG330's as they appear to handle VPN traffic the fastest) and will be able to move our older SG's to replace the REDs. As I'm a visual, hands on, learner, are there any videos or diagram examples out there for setting up manual/split?
Right now our setup is as follows (ignore the orange double arrows):
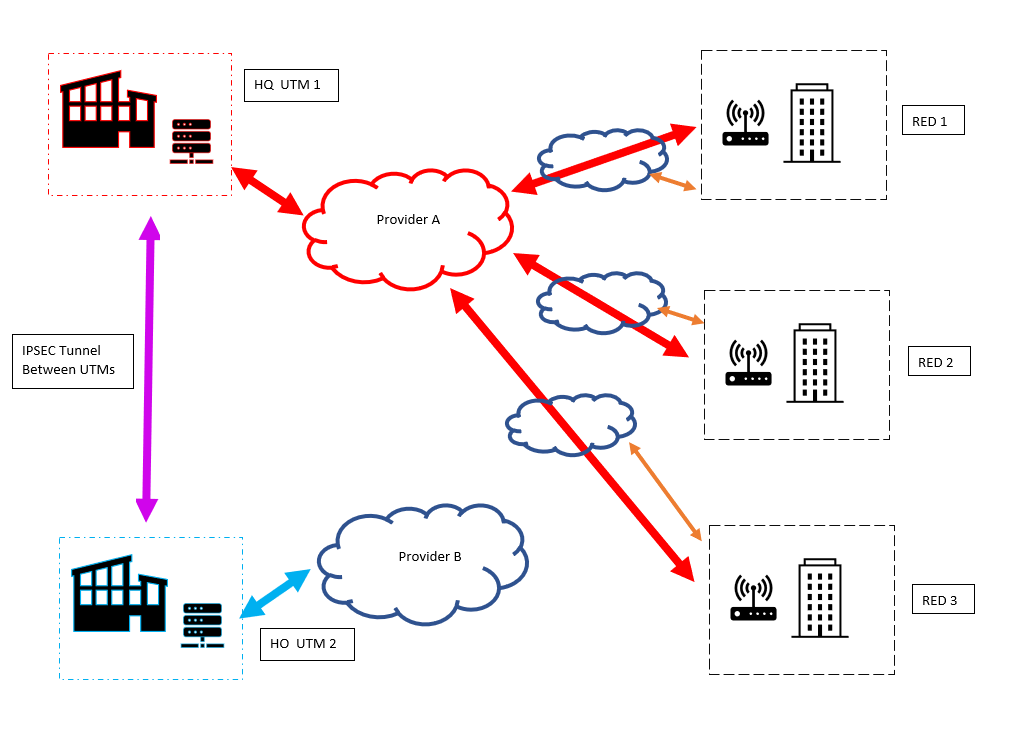
I would like the manual/split (orange double arrows) to happen when the tunnel to HQ goes down for the REDs, but only for IPV4 internet. I'm guessing that at this point, the network at each site with the REDs in place are subject to only their "internal protections"? As the HO and the REDs are on the same provider (also who may be the secondary at HQ eventually), if I get them to mesh the networks together, would it be possible to use the UTM there (UTM 2) as the failover instead? My best guess is no, as it wouldn't contain the configuration information for the REDs (even if they were created manually on this UTM)?
I'll be looking into SD-WAN or failover for UTMs shortly as well, so if there is any added reading recommended feel free to pass those along. Ultimately if I can convince TPTB to get a consultant to assist *cough*Bob*cough* with the swaps when they happen then of course I'll only need the material for learning.
-Dave
This thread was automatically locked due to age.


