Hi,
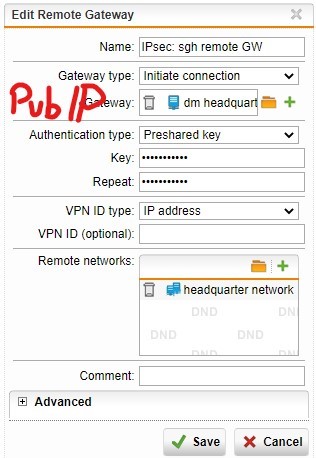
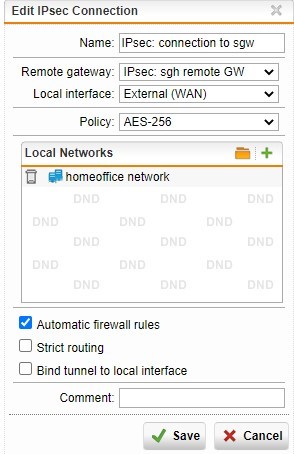
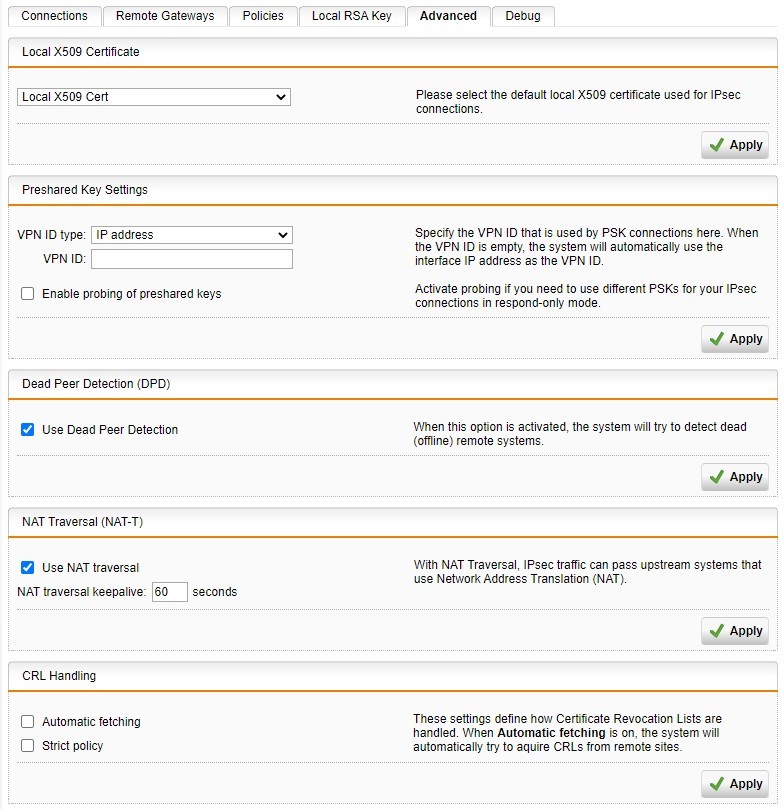
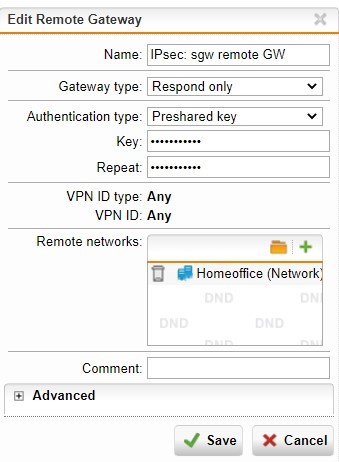
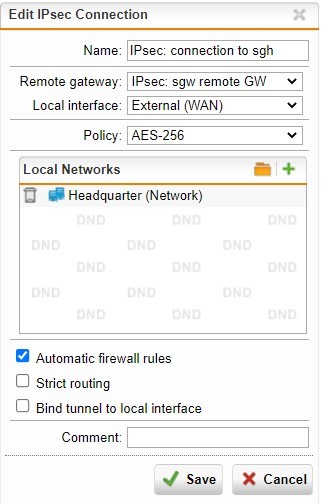
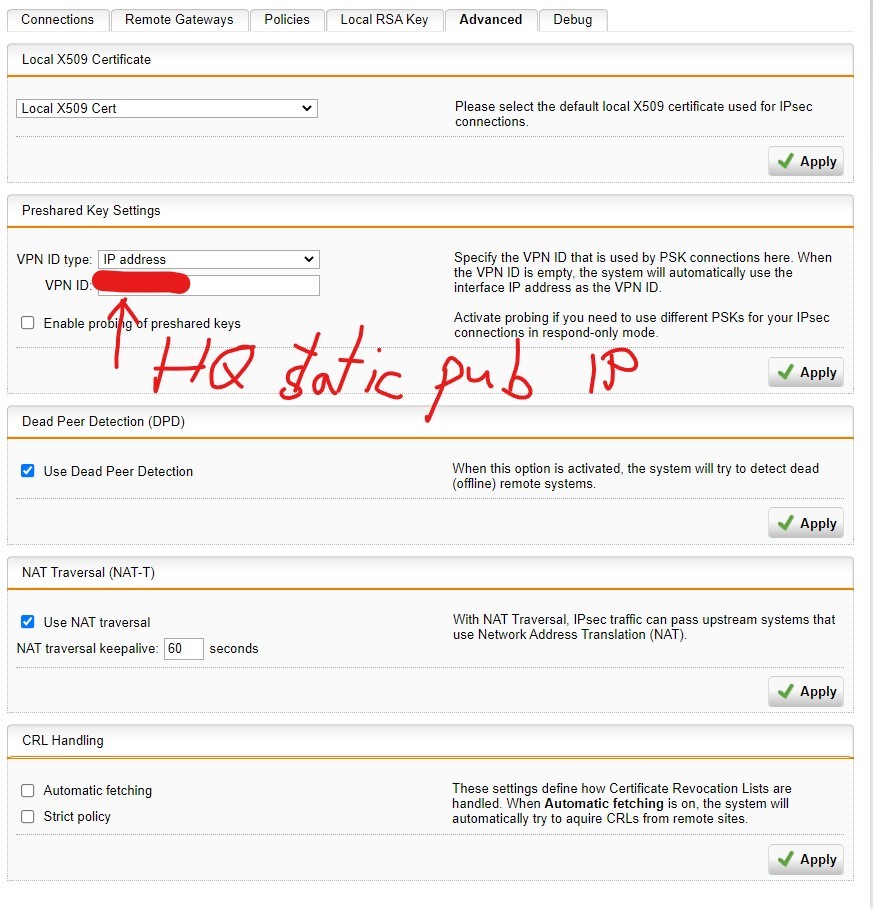
I have a SSL site-to-site VPN connection between headquarter and branch office.
What do I need to set to get ALL traffic from branch office routed through headquarter GW? I cannot find a "default gateway" option.
Thank you very much for help,
Alex
This thread was automatically locked due to age.