Hello,
we have a Sophos UTM 9 SG550 running on latest Firmware 9.709-3. We are using Sophos Connect VPN Client version 2.1.20 ( latest ).
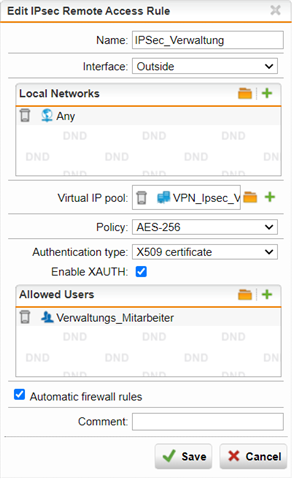
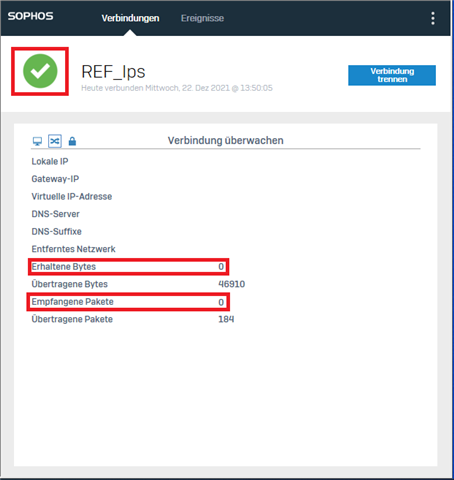
We have Remote Access IPSec setup but for some reason some clients when connected ( from their Home ) will not receive any Bytes and Packets while being able to send them and even ping the Interface of the Firewall. When that happens they are like in some sort of Limbo where they have no connection to any of our networks.
The weirdest thing is that sometimes it works, other times it doesn't ( same users have it working and then it simply doesn't work anymore ). For Some users it helps when we change the MTU Size of the Sophos TAP Adapter ( in Windows ) to "1300" but for others nothing seems to help. The affected users will get some sort of Standard IP ( like 192.168.0.1 ), not from the virtual Pool defined in the IPSec Connection.
It doesn't matter which Laptop they use, seems to affect all kinds. We even tried to disable the Windows Firewall on the clients to no avail. I have tried to search the logs for hours and there just aren't any errors.
Even on my Test Laptop where I have 3 Different Profiles ( each Profile is in a different OU in the Active Directory ) sometimes for no reason one just stops working.
Our SSL Remote Access ( with OpenVPN ) works completely fine without ever giving any problems. But since you can only create one IP Pool in the SSL Connection we have IPSec Connection setup for a different Group of people.
Firewall CPU or RAM are also not a problem since CPU usage barely ever goes beyond 10%.
I have searched for many hours and lost so much time with this weird thing, can somebody point me in some direction of where I should start looking ? ( I searched literally everywhere and everything I can think of )
I have added a part of a Log from the Client's side once trying to connect IPSec and screenshots from IPSec configuration and Sophos Connect Client where it shows that it is sending Packets but not receiving them. ( which goes forever, no matter how long I let it be nothing changes )
2022-02-22 03:56:20PM 14[LIB] TAP-Windows driver version 1.0 available.
2022-02-22 03:56:20PM 25[KNL] interface 11 'Sophos TAP Adapter' changed state from Down to Up
2022-02-22 03:56:22PM 14[CFG] added vici connection: REF_IpsRoaIpsecverwa3
2022-02-22 03:56:22PM 13[CFG] vici initiate CHILD_SA 'REF_IpsRoaIpsecverwa3-tunnel-1'
2022-02-22 03:56:22PM 12[IKE] <REF_IpsRoaIpsecverwa3|10> initiating Main Mode IKE_SA REF_IpsRoaIpsecverwa3[10] to SOPHOSFIREWALL
2022-02-22 03:56:22PM 12[ENC] <REF_IpsRoaIpsecverwa3|10> generating ID_PROT request 0 [ SA V V V V V ]
2022-02-22 03:56:22PM 12[NET] <REF_IpsRoaIpsecverwa3|10> sending packet: from 172.16.7.36[64538] to SOPHOSFIREWALL[500] (180 bytes)
2022-02-22 03:56:22PM 10[NET] <REF_IpsRoaIpsecverwa3|10> received packet: from SOPHOSFIREWALL[500] to 172.16.7.36[64538] (176 bytes)
2022-02-22 03:56:22PM 10[ENC] <REF_IpsRoaIpsecverwa3|10> parsed ID_PROT response 0 [ SA V V V V V ]
2022-02-22 03:56:22PM 10[IKE] <REF_IpsRoaIpsecverwa3|10> received strongSwan vendor ID
2022-02-22 03:56:22PM 10[IKE] <REF_IpsRoaIpsecverwa3|10> received Cisco Unity vendor ID
2022-02-22 03:56:22PM 10[IKE] <REF_IpsRoaIpsecverwa3|10> received XAuth vendor ID
2022-02-22 03:56:22PM 10[IKE] <REF_IpsRoaIpsecverwa3|10> received DPD vendor ID
2022-02-22 03:56:22PM 10[IKE] <REF_IpsRoaIpsecverwa3|10> received NAT-T (RFC 3947) vendor ID
2022-02-22 03:56:22PM 10[CFG] <REF_IpsRoaIpsecverwa3|10> selected proposal: IKE:AES_CBC_256/HMAC_MD5_96/PRF_HMAC_MD5/MODP_1536
2022-02-22 03:56:22PM 10[ENC] <REF_IpsRoaIpsecverwa3|10> generating ID_PROT request 0 [ KE No NAT-D NAT-D ]
2022-02-22 03:56:22PM 10[NET] <REF_IpsRoaIpsecverwa3|10> sending packet: from 172.16.7.36[64538] to SOPHOSFIREWALL[500] (300 bytes)
2022-02-22 03:56:22PM 09[NET] <REF_IpsRoaIpsecverwa3|10> received packet: from SOPHOSFIREWALL[500] to 172.16.7.36[64538] (284 bytes)
2022-02-22 03:56:22PM 09[ENC] <REF_IpsRoaIpsecverwa3|10> parsed ID_PROT response 0 [ KE No NAT-D NAT-D ]
2022-02-22 03:56:22PM 09[IKE] <REF_IpsRoaIpsecverwa3|10> faking NAT situation to enforce UDP encapsulation
2022-02-22 03:56:22PM 09[IKE] <REF_IpsRoaIpsecverwa3|10> sending cert request for "OURCECRT"
2022-02-22 03:56:22PM 09[IKE] <REF_IpsRoaIpsecverwa3|10> authentication of 'TESTACCOUNT' (myself) successful
2022-02-22 03:56:22PM 09[ENC] <REF_IpsRoaIpsecverwa3|10> generating ID_PROT request 0 [ ID SIG CERTREQ ]
2022-02-22 03:56:22PM 09[NET] <REF_IpsRoaIpsecverwa3|10> sending packet: from 172.16.7.36[64539] to SOPHOSFIREWALL[4500] (524 bytes)
2022-02-22 03:56:23PM 11[NET] <REF_IpsRoaIpsecverwa3|10> received packet: from SOPHOSFIREWALL[4500] to 172.16.7.36[64539] (2172 bytes)
2022-02-22 03:56:23PM 11[ENC] <REF_IpsRoaIpsecverwa3|10> parsed ID_PROT response 0 [ ID CERT SIG ]
2022-02-22 03:56:23PM 11[IKE] <REF_IpsRoaIpsecverwa3|10> received end entity cert "OURCECRT"
2022-02-22 03:56:23PM 11[CFG] <REF_IpsRoaIpsecverwa3|10> using certificate "OURCECRT"
2022-02-22 03:56:23PM 11[CFG] <REF_IpsRoaIpsecverwa3|10> using trusted ca certificate "OURCECRT"
2022-02-22 03:56:23PM 11[CFG] <REF_IpsRoaIpsecverwa3|10> reached self-signed root ca with a path length of 0
2022-02-22 03:56:23PM 11[IKE] <REF_IpsRoaIpsecverwa3|10> authentication of 'VPNDOMAIN' with RSA_EMSA_PKCS1_NULL successful
2022-02-22 03:56:23PM 12[NET] <REF_IpsRoaIpsecverwa3|10> received packet: from SOPHOSFIREWALL[4500] to 172.16.7.36[64539] (76 bytes)
2022-02-22 03:56:23PM 12[ENC] <REF_IpsRoaIpsecverwa3|10> parsed TRANSACTION request 276855442 [ HASH CPRQ(X_USER X_PWD) ]
2022-02-22 03:56:23PM 12[ENC] <REF_IpsRoaIpsecverwa3|10> generating TRANSACTION response 276855442 [ HASH CPRP(X_USER X_PWD) ]
2022-02-22 03:56:23PM 12[NET] <REF_IpsRoaIpsecverwa3|10> sending packet: from 172.16.7.36[64539] to SOPHOSFIREWALL[4500] (92 bytes)
2022-02-22 03:56:23PM 11[NET] <REF_IpsRoaIpsecverwa3|10> received packet: from SOPHOSFIREWALL[4500] to 172.16.7.36[64539] (60 bytes)
2022-02-22 03:56:23PM 11[ENC] <REF_IpsRoaIpsecverwa3|10> parsed TRANSACTION request 2454260142 [ HASH CPS(X_STATUS) ]
2022-02-22 03:56:23PM 11[IKE] <REF_IpsRoaIpsecverwa3|10> XAuth authentication of 'USER' (myself) successful
2022-02-22 03:56:23PM 11[IKE] <REF_IpsRoaIpsecverwa3|10> IKE_SA REF_IpsRoaIpsecverwa3[10] established between 172.16.7.36[TESTACCOUNT]...SOPHOSFIREWALL[VPNDOMAIN]
2022-02-22 03:56:23PM 11[IKE] <REF_IpsRoaIpsecverwa3|10> scheduling rekeying in 6951s
2022-02-22 03:56:23PM 11[IKE] <REF_IpsRoaIpsecverwa3|10> maximum IKE_SA lifetime 7692s
2022-02-22 03:56:23PM 11[ENC] <REF_IpsRoaIpsecverwa3|10> generating TRANSACTION response 2454260142 [ HASH CPA(X_STATUS) ]
2022-02-22 03:56:23PM 11[NET] <REF_IpsRoaIpsecverwa3|10> sending packet: from 172.16.7.36[64539] to SOPHOSFIREWALL[4500] (76 bytes)
2022-02-22 03:56:23PM 11[ENC] <REF_IpsRoaIpsecverwa3|10> generating TRANSACTION request 941346236 [ HASH CPRQ(ADDR DNS) ]
2022-02-22 03:56:23PM 11[NET] <REF_IpsRoaIpsecverwa3|10> sending packet: from 172.16.7.36[64539] to SOPHOSFIREWALL[4500] (76 bytes)
2022-02-22 03:56:23PM 09[NET] <REF_IpsRoaIpsecverwa3|10> received packet: from SOPHOSFIREWALL[4500] to 172.16.7.36[64539] (108 bytes)
2022-02-22 03:56:23PM 09[ENC] <REF_IpsRoaIpsecverwa3|10> parsed TRANSACTION response 941346236 [ HASH CPRP(ADDR DNS DNS U_DEFDOM) ]
2022-02-22 03:56:23PM 09[IKE] <REF_IpsRoaIpsecverwa3|10> Adding DNS server OURDNS1 to the TAP adapter
2022-02-22 03:56:23PM 09[IKE] <REF_IpsRoaIpsecverwa3|10> OURDNS1 not in servers list, doing add
2022-02-22 03:56:23PM 09[IKE] <REF_IpsRoaIpsecverwa3|10> DNS server IP address OURDNS1 is already in the DNS server list
2022-02-22 03:56:23PM 09[IKE] <REF_IpsRoaIpsecverwa3|10> Adding DNS server OURDNS2 to the TAP adapter
2022-02-22 03:56:23PM 09[IKE] <REF_IpsRoaIpsecverwa3|10> OURDNS2 not in servers list, doing add
2022-02-22 03:56:23PM 09[IKE] <REF_IpsRoaIpsecverwa3|10> DNS server IP address OURDNS2 is already in the DNS server list
2022-02-22 03:56:23PM 09[IKE] <REF_IpsRoaIpsecverwa3|10> Setting DNS suffix OURDOMAIN into the TAP adapter
2022-02-22 03:56:23PM 09[IKE] <REF_IpsRoaIpsecverwa3|10> Domain suffix OURDOMAIN not in virtual adapter - adding
2022-02-22 03:56:23PM 09[IKE] <REF_IpsRoaIpsecverwa3|10> Domain suffix OURDOMAIN added to virtual adapter
2022-02-22 03:56:23PM 09[IKE] <REF_IpsRoaIpsecverwa3|10> installing new virtual IP 192.168.6.10 on interface {47A51965-63DE-4CB6-80D1-965C55252C7B}
2022-02-22 03:56:23PM 09[KNL] <REF_IpsRoaIpsecverwa3|10> Adding virtual IP 192.168.6.10
2022-02-22 03:56:23PM 09[KNL] <REF_IpsRoaIpsecverwa3|10> 192.168.6.10 added to addresses list
2022-02-22 03:56:23PM 09[KNL] <REF_IpsRoaIpsecverwa3|10> 192.168.6.10 is not yet assigned to the virtual adapter - adding
2022-02-22 03:56:23PM 09[ENC] <REF_IpsRoaIpsecverwa3|10> generating QUICK_MODE request 3420046745 [ HASH SA No KE ID ID ]
2022-02-22 03:56:23PM 09[NET] <REF_IpsRoaIpsecverwa3|10> sending packet: from 172.16.7.36[64539] to SOPHOSFIREWALL[4500] (380 bytes)
2022-02-22 03:56:23PM 16[NET] <REF_IpsRoaIpsecverwa3|10> received packet: from SOPHOSFIREWALL[4500] to 172.16.7.36[64539] (348 bytes)
2022-02-22 03:56:23PM 16[ENC] <REF_IpsRoaIpsecverwa3|10> parsed QUICK_MODE response 3420046745 [ HASH SA No KE ID ID ]
2022-02-22 03:56:23PM 16[CFG] <REF_IpsRoaIpsecverwa3|10> selected proposal: ESP:AES_CBC_256/HMAC_MD5_96/MODP_1536/NO_EXT_SEQ
2022-02-22 03:56:23PM 16[CHD] <REF_IpsRoaIpsecverwa3|10> CHILD_SA REF_IpsRoaIpsecverwa3-tunnel-1{10} state change: CREATED => INSTALLING
2022-02-22 03:56:23PM 16[CHD] <REF_IpsRoaIpsecverwa3|10> using AES_CBC for encryption
2022-02-22 03:56:23PM 16[CHD] <REF_IpsRoaIpsecverwa3|10> using HMAC_MD5_96 for integrity
2022-02-22 03:56:23PM 16[CHD] <REF_IpsRoaIpsecverwa3|10> adding inbound ESP SA
2022-02-22 03:56:23PM 16[CHD] <REF_IpsRoaIpsecverwa3|10> SPI 0x503a74a4, src SOPHOSFIREWALL dst 172.16.7.36
2022-02-22 03:56:23PM 16[CHD] <REF_IpsRoaIpsecverwa3|10> adding outbound ESP SA
2022-02-22 03:56:23PM 16[CHD] <REF_IpsRoaIpsecverwa3|10> SPI 0x9a7447c4, src 172.16.7.36 dst SOPHOSFIREWALL
2022-02-22 03:56:23PM 16[KNL] <REF_IpsRoaIpsecverwa3|10> installing route 0.0.0.0/0 src 192.168.6.10 gateway 169.254.128.128 dev {5BB8B74D-9DDB-425A-A371-61A0A63B7494}
2022-02-22 03:56:23PM 16[IKE] <REF_IpsRoaIpsecverwa3|10> CHILD_SA REF_IpsRoaIpsecverwa3-tunnel-1{10} established with SPIs 503a74a4_i 9a7447c4_o and TS 192.168.6.10/32 === 0.0.0.0/0
2022-02-22 03:56:23PM 16[CHD] <REF_IpsRoaIpsecverwa3|10> CHILD_SA REF_IpsRoaIpsecverwa3-tunnel-1{10} state change: INSTALLING => INSTALLED
2022-02-22 03:56:23PM 16[ENC] <REF_IpsRoaIpsecverwa3|10> generating QUICK_MODE request 3420046745 [ HASH ]
2022-02-22 03:56:23PM 16[NET] <REF_IpsRoaIpsecverwa3|10> sending packet: from 172.16.7.36[64539] to SOPHOSFIREWALL[4500] (60 bytes)
2022-02-22 03:56:30PM 08[ESP] unsupported IP version
2022-02-22 03:56:30PM 09[CFG] vici terminate IKE_SA 'REF_IpsRoaIpsecverwa3'
2022-02-22 03:56:30PM 27[KNL] interface 11 'Sophos TAP Adapter' changed state from Up to Down
2022-02-22 03:56:30PM 27[KNL] 169.254.202.155 disappeared from interface 11 'Sophos TAP Adapter'
2022-02-22 03:56:30PM 10[CHD] <REF_IpsRoaIpsecverwa3|10> CHILD_SA REF_IpsRoaIpsecverwa3-tunnel-1{10} state change: INSTALLED => DELETING
2022-02-22 03:56:30PM 10[IKE] <REF_IpsRoaIpsecverwa3|10> closing CHILD_SA REF_IpsRoaIpsecverwa3-tunnel-1{10} with SPIs 503a74a4_i (0 bytes) 9a7447c4_o (628 bytes) and TS 192.168.6.10/32 === 0.0.0.0/0
2022-02-22 03:56:30PM 10[CHD] <REF_IpsRoaIpsecverwa3|10> CHILD_SA REF_IpsRoaIpsecverwa3-tunnel-1{10} state change: DELETING => DELETED
2022-02-22 03:56:30PM 10[CHD] <REF_IpsRoaIpsecverwa3|10> CHILD_SA REF_IpsRoaIpsecverwa3-tunnel-1{10} state change: DELETED => DESTROYING
2022-02-22 03:56:30PM 10[IKE] <REF_IpsRoaIpsecverwa3|10> sending DELETE for ESP CHILD_SA with SPI 503a74a4
2022-02-22 03:56:30PM 10[ENC] <REF_IpsRoaIpsecverwa3|10> generating INFORMATIONAL_V1 request 1026805056 [ HASH D ]
2022-02-22 03:56:30PM 10[NET] <REF_IpsRoaIpsecverwa3|10> sending packet: from 172.16.7.36[64539] to SOPHOSFIREWALL[4500] (76 bytes)
2022-02-22 03:56:30PM 10[IKE] <REF_IpsRoaIpsecverwa3|10> deleting IKE_SA REF_IpsRoaIpsecverwa3[10] between 172.16.7.36[TESTACCOUNT]...SOPHOSFIREWALL[VPNDOMAIN]
2022-02-22 03:56:30PM 10[IKE] <REF_IpsRoaIpsecverwa3|10> sending DELETE for IKE_SA REF_IpsRoaIpsecverwa3[10]
2022-02-22 03:56:30PM 10[ENC] <REF_IpsRoaIpsecverwa3|10> generating INFORMATIONAL_V1 request 2202287485 [ HASH D ]
2022-02-22 03:56:30PM 10[NET] <REF_IpsRoaIpsecverwa3|10> sending packet: from 172.16.7.36[64539] to SOPHOSFIREWALL[4500] (92 bytes)
2022-02-22 03:56:30PM 10[IKE] <REF_IpsRoaIpsecverwa3|10> Removing DNS suffix OURDOMAIN from the TAP adapter
2022-02-22 03:56:30PM 10[IKE] <REF_IpsRoaIpsecverwa3|10> Suffix count is 0 - doing remove
2022-02-22 03:56:30PM 10[IKE] <REF_IpsRoaIpsecverwa3|10> removing DNS suffix failed
2022-02-22 03:56:30PM 10[IKE] <REF_IpsRoaIpsecverwa3|10> Removing DNS server OURDNS2 from the TAP adapter
2022-02-22 03:56:30PM 10[IKE] <REF_IpsRoaIpsecverwa3|10> OURDNS2 count is 0, doing remove
2022-02-22 03:56:30PM 10[IKE] <REF_IpsRoaIpsecverwa3|10> Dns server IP address OURDNS2 is already not in the DNS server list
2022-02-22 03:56:30PM 10[IKE] <REF_IpsRoaIpsecverwa3|10> Removing DNS server OURDNS1 from the TAP adapter
2022-02-22 03:56:30PM 10[IKE] <REF_IpsRoaIpsecverwa3|10> OURDNS1 count is 0, doing remove
2022-02-22 03:56:30PM 10[IKE] <REF_IpsRoaIpsecverwa3|10> Dns server IP address OURDNS1 is already not in the DNS server list
2022-02-22 03:56:30PM 10[KNL] <REF_IpsRoaIpsecverwa3|10> Removing virtual IP 192.168.6.10
2022-02-22 03:56:30PM 10[KNL] <REF_IpsRoaIpsecverwa3|10> 192.168.6.10 removed from addresses list
2022-02-22 03:56:30PM 10[KNL] <REF_IpsRoaIpsecverwa3|10> 192.168.6.10 has been removed from the virtual adapter
2022-02-22 03:56:33PM 10[CFG] unloaded private key with id 47754862c50be23b031d195bf22e59138a046b1b
2022-02-22 03:56:33PM 12[CFG] unloaded shared key with id 'REF_IpsRoaIpsecverwa3-user-id'
This thread was automatically locked due to age.


