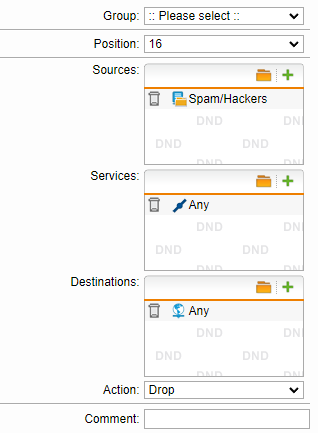
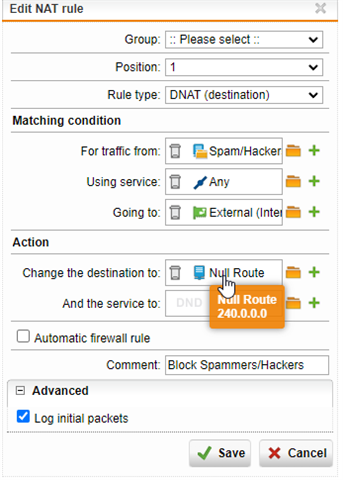
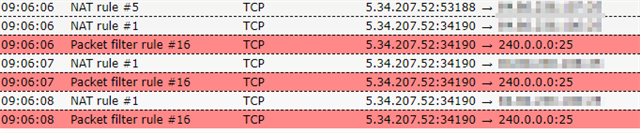
Hello, there is someone spamming our email server and I blocked the IP in two ways in which I'll attach pictures of. One is a basic firewall rule to drop traffic from a list of spammer/hacker IPs. The other is a DNAT rule which takes that same list and is supposed to route the traffic to a random IP that has nothing to do with our network. When I look at the logs, the firewall rule appears to work but the DNAT rule is apparently ALLOWING the traffic to go through and I cannot for the life of me figure out why. I have these rules as high as they can go (firewall starts at 16 because of automatic rules before it). Nat rule #1 is the "black hole" rule and Nat rule #5 is any > smtp > our mail server > destination: our spam firewall. The "going to" IP is our WAN IP. Something else I'm confused on too is that the blocked message from packet filter #16 seems to be the Nat rule because that's the rule that routes traffic to 240.0.0.0; the firewall rule is just set to drop obviously, but the logs seem to show the block coming from the firewall rule and not the NAT? I'm confused. Any ideas? Sorry I am by no means an expert on this device.
This thread was automatically locked due to age.


