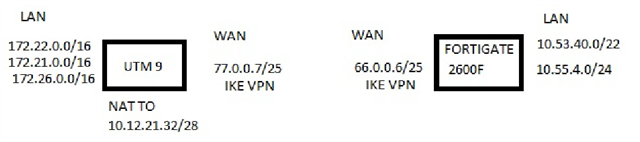
Hi
please help is needed would someone point me in the direction for information on how to set up a NATed VPN on a UTM9?
While i have set up many VPN tunnels having a NATed VPN is very new to me.
Any help greatly appreciated
This thread was automatically locked due to age.