Hello all,
As the UTM 9.705-7 we are using was setup by an MSP and at that time we had Exchange 2010, on premise as well. We've since moved to Exchange online and I handle all the Sophos items now.
Lately we have random users receiving the following pop up when connecting to Exchange through Outlook:
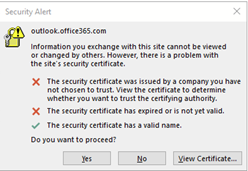
If I view the certificate it pops ups with:
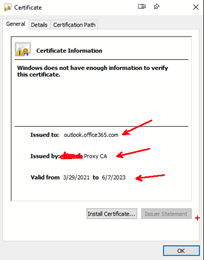
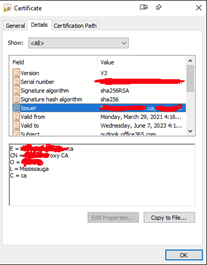
Both the email address that is obscured is from the MSP that no longer exists (they were the original providers before the present MSP), and the CN is [redacted] Proxy CA, which is as far as I can find a cert generated by the UTM.
If I go into the cert manager and browse the users/device I find the same email address and almost the same issuer:
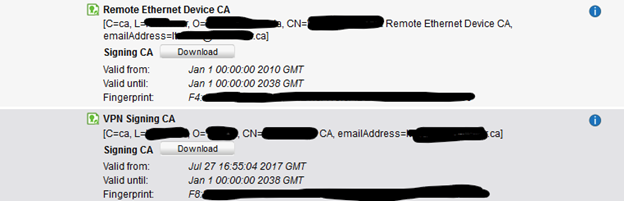
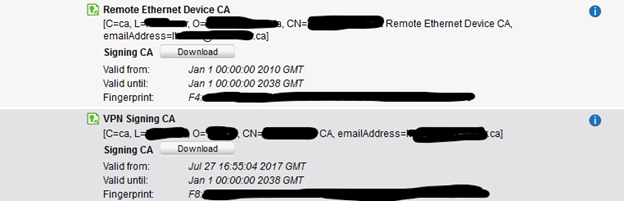
So my questions are:
1 - where should I be able to find the initial cert(s) showing the equivalent CN, supposedly issued by the UTM?
2 - Can I safely update the certificates for all my users and existing certs by recreating them with a "proper" email address?
2a - If I update any/all the certs do my users and their devices need to re-download the cert?
2b - Since we SSL VPN would users need to re-download their configurations?
2c - how if at all, does this effect our RED and IPSec VPNs between UTMS and partners?
3 - We have have valid wildcard certs for our external domains, but our internal domain is a .local with a completely different name. If (and where can I) we add our domain cert to the UTM so that the exceptions for users connecting to the portal aren't needed (external public IP address), will that break anything else?
Thanks all in advance,
Dave
( Sophos and Cert noob )
This thread was automatically locked due to age.


