Hello,
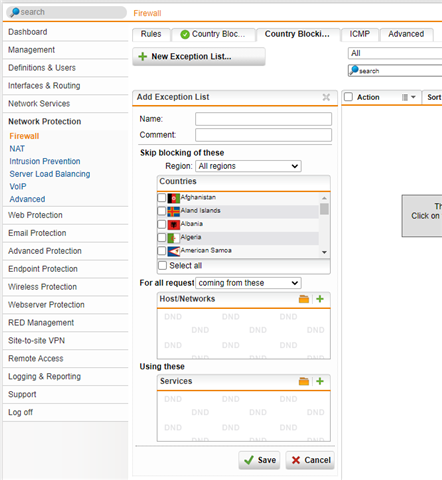
I have a lot of IPs trying to access my External IP on my UTM. I already have ablackhole DNAT Rule added, but I would like to adapt this Rule to be able to permanently block specific IPs / IP Ranges
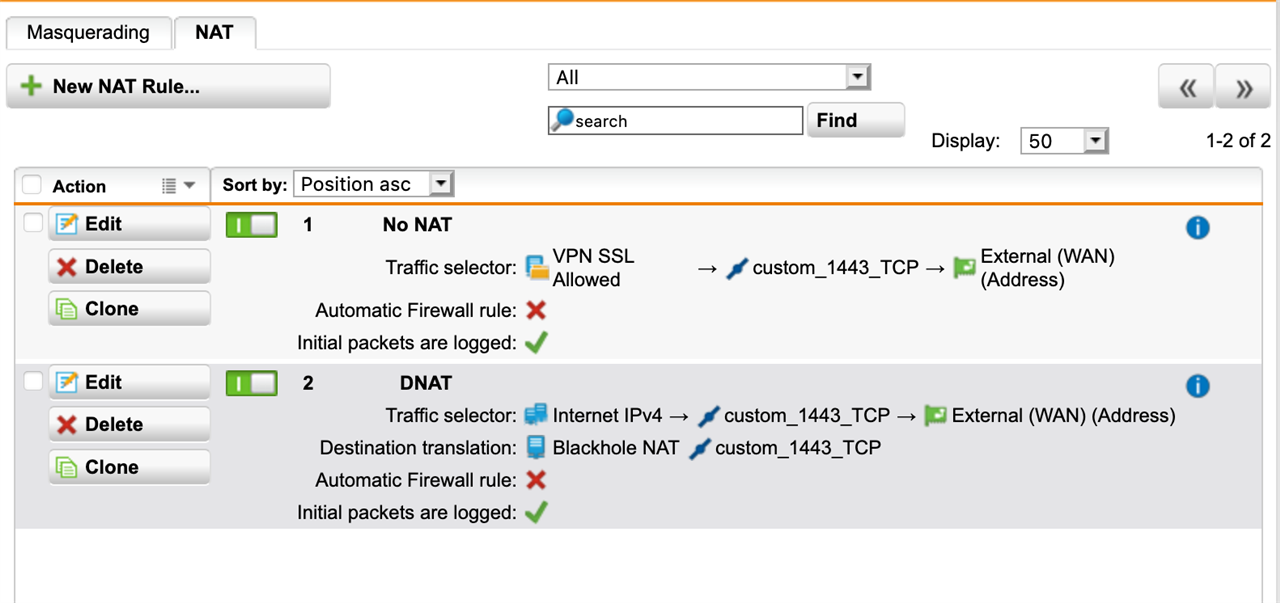
What would be the best way to do this?
Thx
br
Sally
This thread was automatically locked due to age.