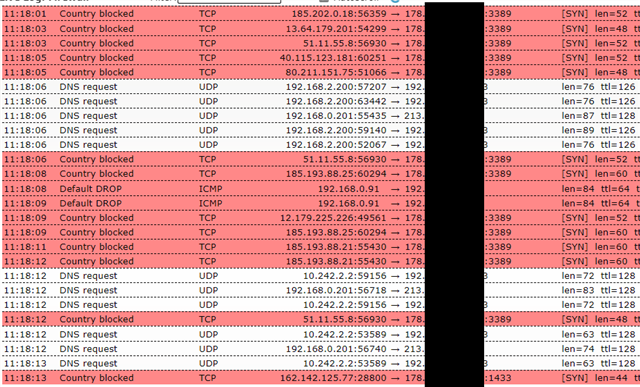
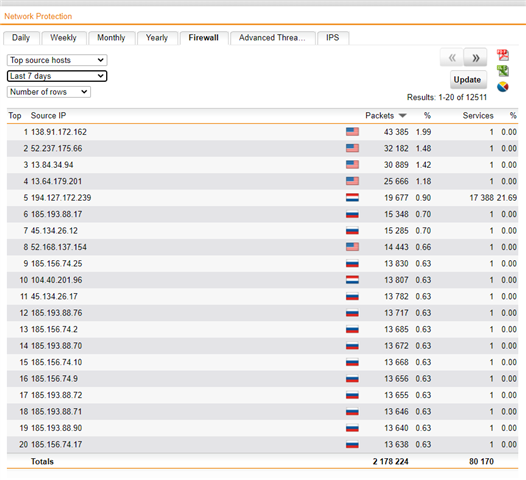
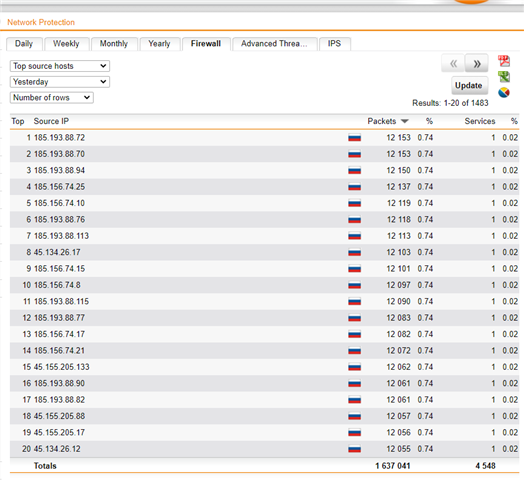
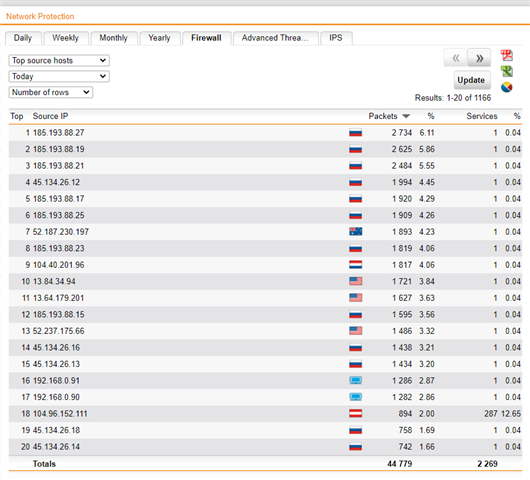
Hello, today I realized that someone is trying to brute force my RDP Server since a few days.
So I switched of the NAT rule for RDP.
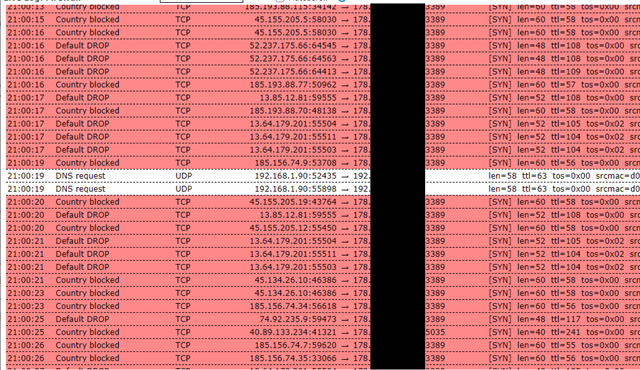
Still the attack keeps going on, the UTM does its work and drops the packets. Since I am getting attacked from multiple IP Adresses, is there anyway to stop this?
Or do I just have to wait until the attacker is stopping it?
Thank you for your thoughts!
This thread was automatically locked due to age.