I'm currently using Uplink Balancing with one active WAN (WAN1) and one standby WAN (WAN-BAK) interface for failover.
I have prepared a WAN2 interface (to another ISP) and would like to add it to active interfaces in order to provide a smooth transition from one ISP to the other.
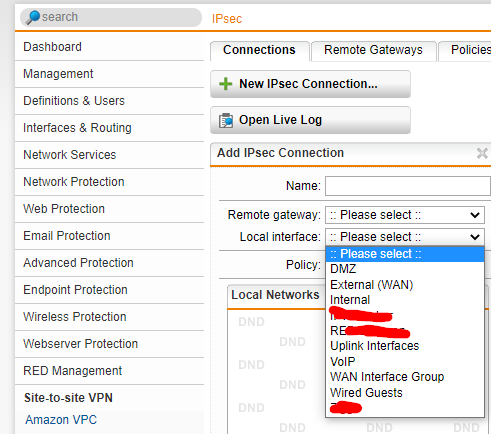
I assume I would loose control regarding which of the active WAN interface is being used for IPSec tunnel connections. My IPSec tunnels can only work with WAN1 since the other site is configured to accept connections only from WAN1.
Is there a way to ensure a certain IPSec tunnel (I currently have 2 of them) uses a certain WAN interface?
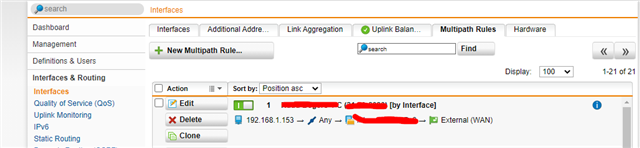
Can this rules/assignment be also done for LAN subnets (I have several of them)?
When everything is in place I would like to have the possibility to move IPSec tunnels and subnets from using WAN1 to using WAN2 one after the other.
Can this be done using Policy Rules? What would be an example configuration for a IPSec tunnel or subnet?
This thread was automatically locked due to age.