Hi All-
Please forgive me for reposting this, however the previous post I had replied to with this (https://community.sophos.com/utm-firewall/f/network-protection-firewall-nat-qos-ips/114954/routing-single-local-host-internet-traffic-through-remote-ipsec-tunnel-gateway) has been locked due to inactivity and I am again revisiting trying to make this work.
Karl-Heinz van Hardeveld and BAlfson - you were the experts in that thread, perhaps you can shed some light on my situation.
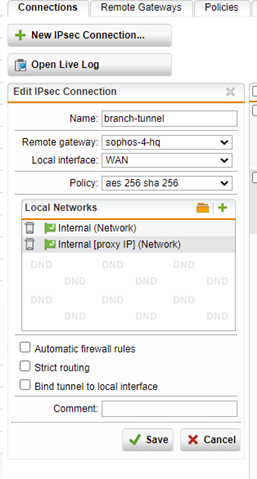
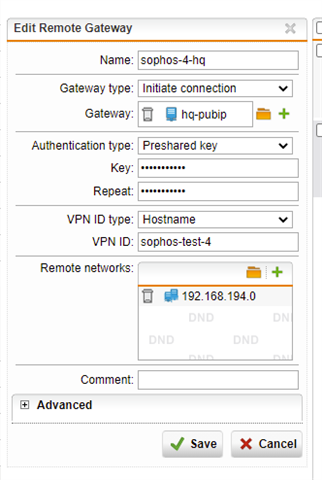
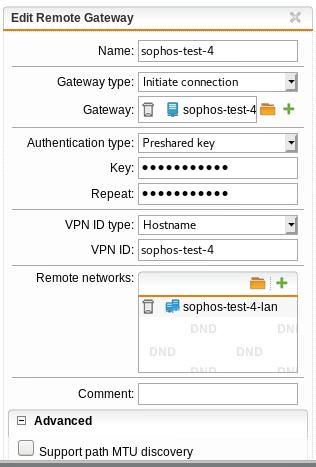
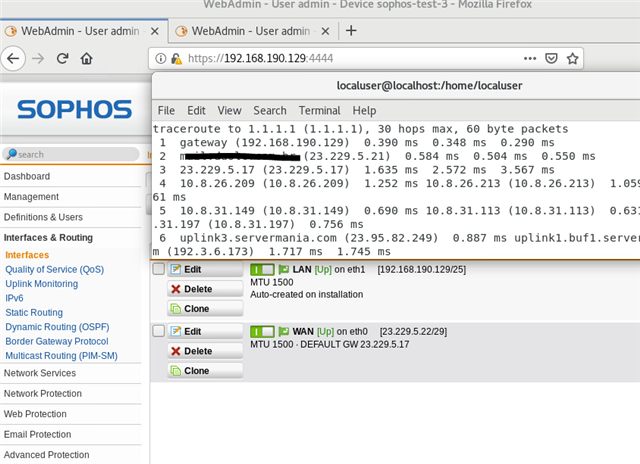
SITE A: is a branch office with 192.168.68.0/23 and 10.0.1.0/24. SITE B is HQ. SITE B has 192.168.64.0/22
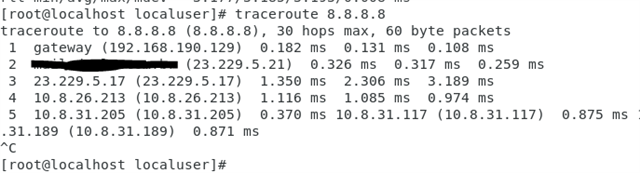
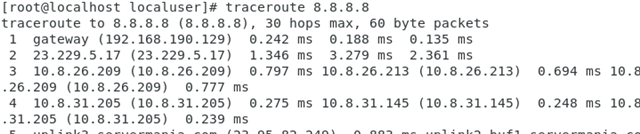
All traffic from SITE A that originates from an IP in 10.0.1.0/24 should traverse the IPSEC tunnel and egress via the SITE B firewall WAN interface.
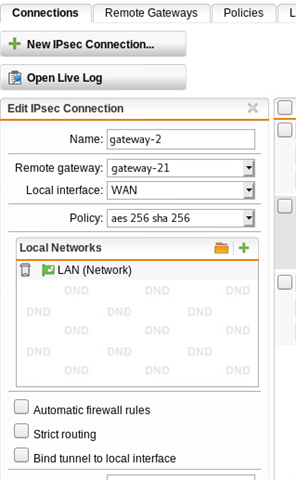
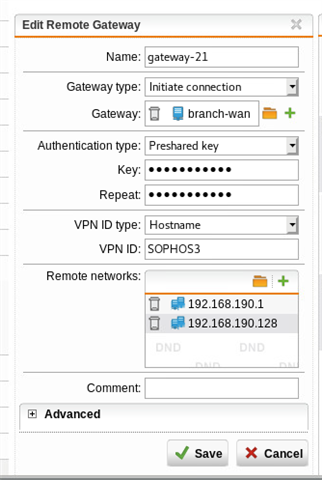
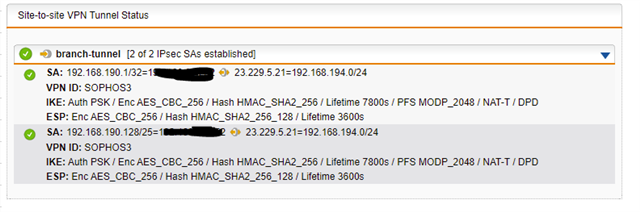
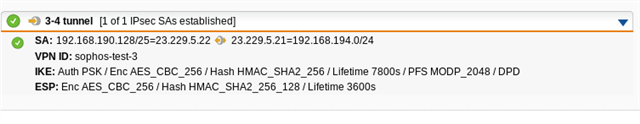
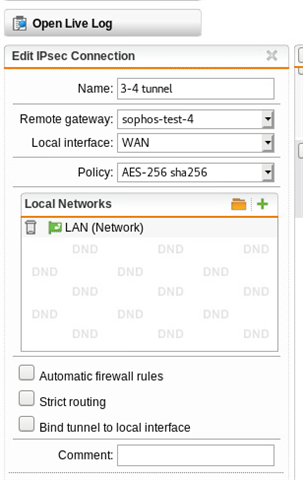
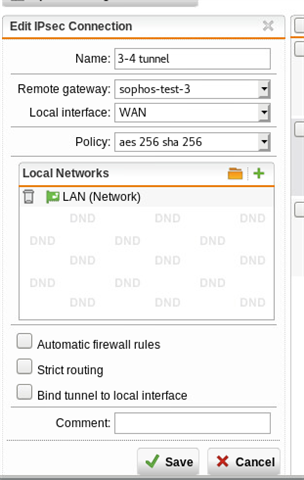
Here is the tunnel status, as you can see, it has established correctly:
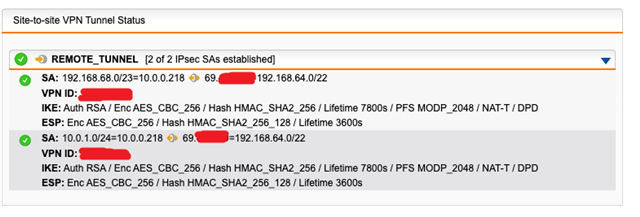
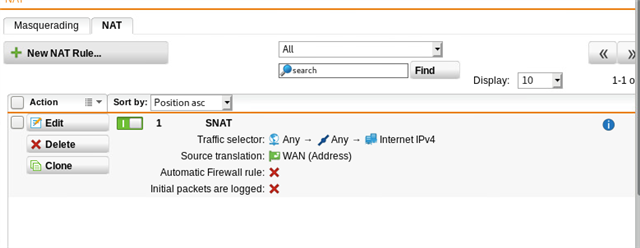
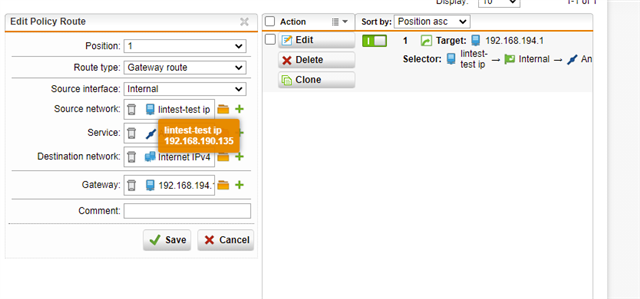
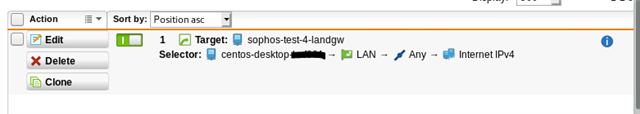
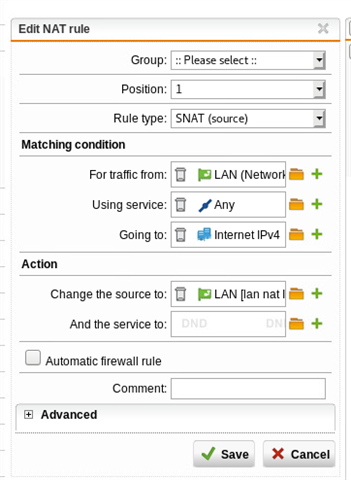
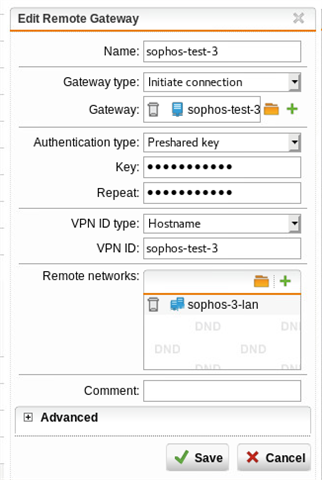
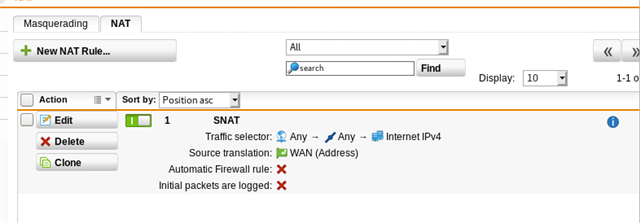
Using either a masquerading or SNAT rule, I can get traffic to exit via the WAN interface at SITE A, but remember, we want this to go back to SITE B first via the tunnel. Per the above thread, I created a PBR on SITE A (BRANCH OFFICE) firewall. NOTE: "Remote_LAN is the internal local IP on the HQ (SITEB) firewall, 192.168.64.1.
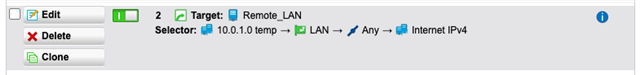
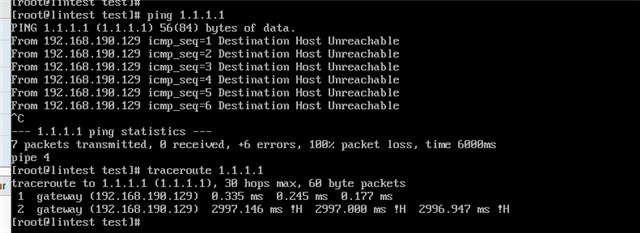
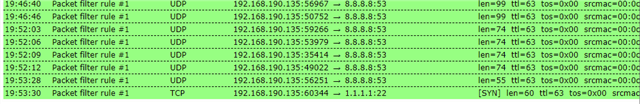
This immediately breaks the internet at SITE A. I can still be on a workstation at 10.0.1.2 and ping 192.168.64.1, but once the above PBR is enabled, internet breaks. No logs are found at the HQ site that originate from the tunnel.
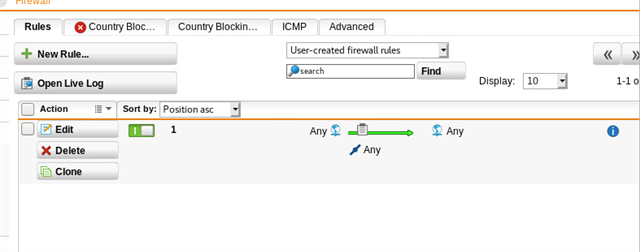
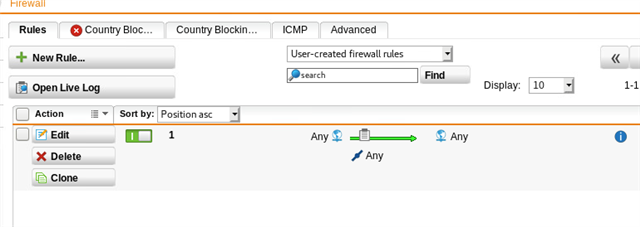
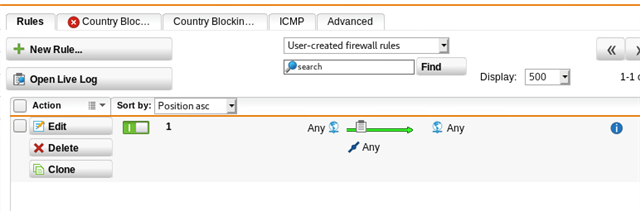
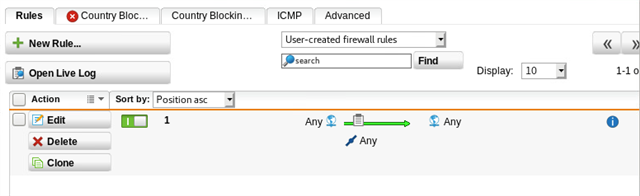
both sites have been tested with an ANY>ANY firewall rule, along with "auto firewall rules" on both sides for the IPSEC tunnel, which makes no difference.
I've also tested iterations of disabling the SNAT rule (and/or masq rule) at the BRANCH site, makes no difference. As soon as the PBR is enabled, internet breaks.
This thread was automatically locked due to age.