I've searched and read other posts about this, but nothing seems to be working for me. Hoping to get some more input and maybe point me in the right direction.
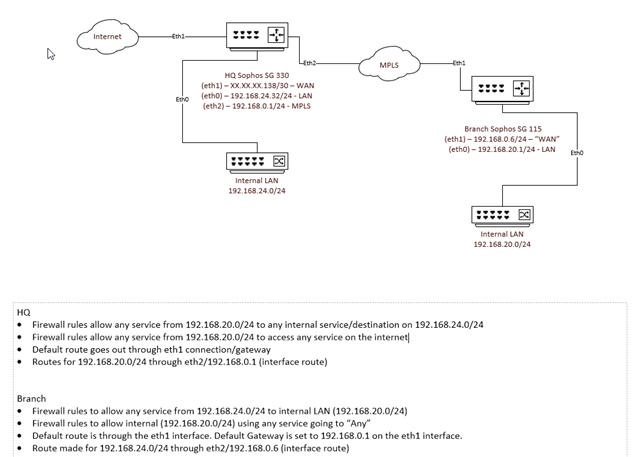
We're replacing the network hardware for a company that has 9 total locations. They are all currently connected via MPLS with the HQ location being the only site that has internet. All other sites feed out through the HQ site. They have Cisco 3800's are each location and we're replacing those with Sophos SG units. We've already successfully replaced the devices at the HQ location and everything is working correctly. We've tried replacing two separate branch locations and have run into the same issue.
The 3800's at each branch location have basic configurations. They have two active interfaces, one for the LAN and one for MPLS. The default route is setup to run through the MPLS interface at HQ (Sophos HQ's MPLS interface - 192.168.0.1).
When we swapped in the Sophos at a branch location today, the WAN Interface was designated as the MPLS interface (192.168.0.6/24), and the LAN was setup for the internal network (192.168.20.1/24). From inside the branch's network, we have no access to anything on the HQ Network and have no internet. When looking at the HQ firewall, we see traffic hitting the firewall and being allowed through, but it seems like traffic isn't returning.
From the HQ side, we can access the branch firewall on the MPLS IP and on the internal LAN IP, but can't access any device beyond the firewall. We can see traffic being dropped when the traffic is destined for the firewall specifically, but we don't see any drops, allows, or anything in the logs when we try and access something beyond the firewall. We verified all firewall rules on the branch firewall are open and allowed, and even set an any/any/any with logging enabled to try and see some entries, but nothing. We also tried it with and without masq rules, but had the same problem (our masq rule was set for internal LAN --> MPLS interface)
I contacted the ISP and had them check the MPLS routing and they said everything looked good. I feel like the issue is on their side and likely has something to do with the fact the hardware changed and something on their end isn't respecting that, but it could still be something with the branch Sophos. When we swap the Cisco back in, everything continues to work, so I don't feel like it's a configuration on the HQ firewall.. When I check arp tables on the HQ firewall, it has some entries for the branch sites internal LAN, but they are listed as "incomplete". After the cisco swap back in, the arp tables display the Cisco MAC correctly.
I've setup MPLS connections betore with Sophos and everything was pretty simple and worked, but we've spent the last two days on this and I'm not really sure what the issue is. Any ideas?
This thread was automatically locked due to age.