Hi Everyone,
Posting this procedure to help other users renewing SSL certificate of WebAdmin and User Portal pages. I am using reference 2 years ago but the link is not available anymore.
A. Create a CSR on Sophos UTM via CLI
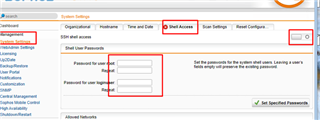
1. Enable Shell access from the GUI. Provide temporary password to root and loginuser accounts
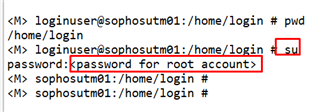
2. Access CLI of Sophos UTM via SSH. Access the UTM console as loginuser, then enter su to login as root. Landing directory of UTM is /home/login.
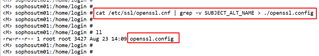
3. Create an openvpn.cnf config file with the following command:
cat /etc/ssl/openssl.cnf | grep -v SUBJECT_ALT_NAME > ./openssl.config
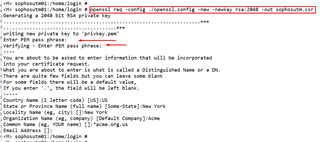
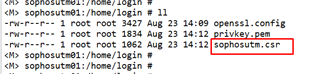
4. Now generate the CSR (Certificate Signing Request) using the previous config file:
openssl req -config ./openssl.config -new -newkey rsa:2048 -out <anyname>.csr
note: In this example sophosutm is the name to create a csr
5. Enter a pass phrase and confirm the pass phrase. (Note: Remember the pass phrase as it will be use in later part)
6. Complete details for the creation of CSR
7. Your CSR will now be saved to /home/login/ directory and can be copied off the UTM using a tool like WinSCP.
The file can also be opened locally on the UTM with the CAT command which can be submitted to CA provider for signing
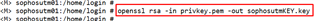
8. On the UTM, decrypt the private key generated earlier under /home/login. It will asked for the pass phrase to decryprt the key
command: openssl rsa -in <Encrypted_key_file.pem> -out < decrypted_output_filename.key>
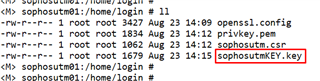
my example--> openssl rsa -in privkey.pem -out sophosutmKEY.key
Once decrypted there will be another file in the working directory
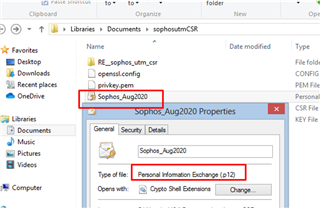
9. Download the SIGNED certificate from the CA provider and then convert it to PKCS12/PFX format. If multiple certs were provided, then open in Notepad and combine into one .crt file.
Another way to combine the certificate and re-create it as .p12 file is using the Sophos CLI
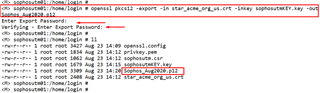
command: openssl pkcs12 -export -in <the_file_you_got_from_the_signing_company>.crt -inkey <decrypted_output_filename.key> -out <new_pk12_filename>.p12.
my example -->openssl pkcs12 -export -in star_acme_org_us.crt -inkey sophosutmKEY.key -out Sophos_Aug2020.p12
Note: Import the signed certificate from the signing company (Certificate Authority like DigiCert) to the default home directory in Sophos UTM using tool such as WINSCP.
Then re-create a .p12 certificate
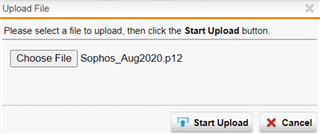
10. Copy the created .p12 file to your desktop (using WINSCP tool) and upload it to Sophos GUI
B. Upload .p12 certificate to GUI
1. Make sure the certificate is saved in #pkcs12 format, and remember the password as well.
2. In Sophos WebAdmin, browse to Remote Access > Certificate Management. Click "New Certificate"
Enter a new name for the certificate (e.g. ACME_CERT_2020)
Choose Upload in the method field.
Browse for the .p12 file on your local system
Enter the password in the password field. Click "Save"
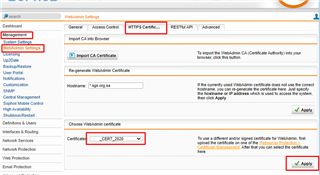
3. Change the certificate for WebAdmin access. Navigate to Management > WebAdmin Settings > HTTPS Certificate. Go over WebAdmin certificate, select the certificate defined in above step, then click Apply
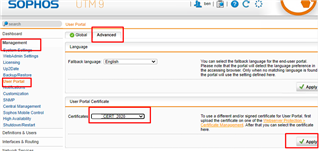
4. Change the certificate for User Portal access. Navigate to Management > User Portal> Advanced. Go over User Portal Certificate section, select the certificate defined in above step, then click Apply
5. Test and verify
HTH
Vhince
This thread was automatically locked due to age.