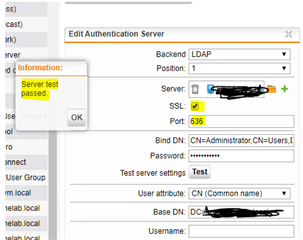
Source https://help.teradici.com/s/article/1707
Run the powershell script and set LDAP SSL option on port 636 and it works. I only changed the fixed domain name to dynamic. It just reads the domain name where the script is running.
I tested it on Microsoft Server 2019 but should work on most Server versions.
If you want to set-and-forget just schedule this script just before the expiration date of the certificate. The script runs just a few seconds :-)
#$domain_name = "mydomain.com"
$domain = Get-ADDomain
$domain_name = $domain.DNSRoot
$dns_name = $env:computername + '.' + $domain_name;
$mycert=New-SelfSignedCertificate -DnsName $dns_name -CertStoreLocation cert:/LocalMachine/My;
$thumbprint=($mycert.Thumbprint | Out-String).Trim();$certStoreLoc='HKLM:/Software/Microsoft/Cryptography/Services/NTDS/SystemCertificates/My/Certificates';
if (!(Test-Path $certStoreLoc)){
New-Item $certStoreLoc -Force;
};
Copy-Item -Path HKLM:/Software/Microsoft/SystemCertificates/My/Certificates/$thumbprint -Destination $certStoreLoc;
P.S. Setting the option LDAP to ACTIVE DIRECTORY here is working aswell...
This thread was automatically locked due to age.